Kentik Blog: DDoS Protection












BGP Flowspec Doesn't Suck. We're Just Using it Wrong.
BGP Flowspec is one of the critical technologies gaining traction in DDoS mitigation strategies. In this article, Justin Ryburn outlines the adoption rates and best practices of this emerging and effective DDoS mitigation tool.
Understanding DDoS Attacks: Motivation and Impact
DDoS attacks disrupt services and damage reputations, with motivations ranging from political to personal. These attacks can also mask more severe security breaches, so early detection and mitigation are crucial. Learn how Kentik provides a solution by analyzing enriched NetFlow data to identify and mitigate DDoS threats.
Securing Your Network Against Attacks: Prevent, Detect, and Mitigate Cyberthreats
As networks become distributed and virtualized, the points at which they can be made vulnerable, or their threat surface, expands dramatically. Learn best practices for preventing, detecting, and mitigating the impact of cyberthreats.
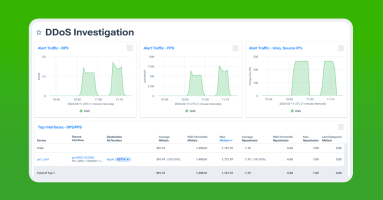
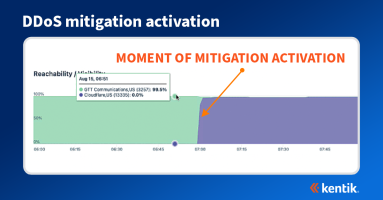
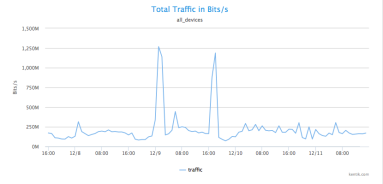
How Kentik Visualizes the BGP Propagation of a DDoS Mitigation
At first glance, a DDoS attack may seem less sophisticated than other types of network attacks, but its effects can be devastating. Visibility into the attack and mitigation is therefore critical for any organization with a public internet presence. Learn how to use Kentik to see the propagation of BGP announcements on the public internet before, during, and after the DDoS attack mitigation.
Webinar recap: A NetOps guide to DDoS defense
Didn’t have time to watch our NetOps guide to DDoS defense webinar with Cloudflare? This blog recaps what was presented and discussed.
8 reasons why network observability is critical for DDoS detection and mitigation
Learn eight ways that network monitoring can be critical for DDoS detection and mitigation.
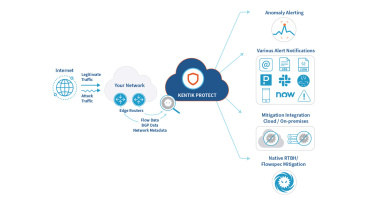
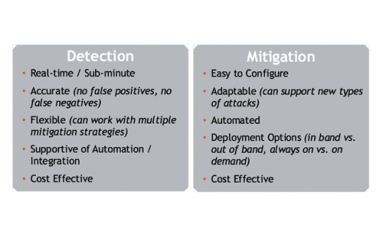
Automated, Accurate, Flexible DDoS Detection and Mitigation
From a threat actor’s side, launching a DDoS attack is both easy and cheap. For a business, it’s costly, disruptive and comes with big hurdles for effective detection and mitigation. Kentik Protect can help.
How Zoom Uses Kentik for Network Visibility, Performance, Peering Analytics & Improved Customer Support
Learn how enterprise video communications leader, Zoom, uses Kentik for network visibility, performance, peering analytics and improved customer support. Zoom’s Alex Guerrero, senior manager of SaaS operations, and Mike Leis, senior network engineer, share how they use Kentik to help Zoom deliver “frictionless meetings.”
How Race Communications Used Kentik to Stop Mirai Botnet Infection and Abuse
Customer success engineer Dan Kelly explains how Race Communications used Kentik’s powerful network analytics to identify malicious traffic associated with the Mirai botnet, determine which of Race Communications’ customer IP addresses were being exploited, save its online IP reputation and fend off other types of DDoS and botnet attacks.
DDoS Protection in the Wild Wild West
The Internet is the wild wild west — and the pace of DDoS attacks is not letting up. But thanks to recent advances in streaming telemetry, network visibility, and Big Data, the good guys are armed with the weapons they need to maintain the peace.
The Future of DDoS Protection in an IoT World
IoT represents a massive threat to network infrastructure, as seen in widely publicized IoT-based DDoS attacks like Mirai. So what needs to happen to safeguard our devices and networks from participating in these botnet attacks? And how can IoT device originated attacks get quickly identified and stopped by network operators? In this post, we discuss scalable IoT DDoS protection.
Monitoring DNS with Kentik
Domain Name Server (DNS) is often overlooked, but it’s one of the most critical pieces of Internet infrastructure. As driven home by last October’s crippling DDoS attack against Dyn, the web can’t function unless DNS resolves hostnames to their underlying IP addresses. In this post we look at how combining Kentik’s software host agent with Dashboards in Kentik gives you the tools you need to ensure DNS availability and performance.
Kentik Detect Alerting: Configuring Alert Policies
Operating a network means staying on top of constant changes in traffic patterns. With legacy network monitoring tools, you often can’t see these changes as they happen. Instead you need a comprehensive visibility solution that includes real-time anomaly detection. Kentik Detect fits the bill with a policy-based alerting system that continuously evaluates incoming flow data. This post provides an overview of system features and configuration.
Why Large Enterprises Need Modern DDoS Defense
Today’s increased reliance on cloud and distributed application architectures means that denial of just a single critical dependency can shut down Web availability and revenue. In this post we look at what that means for large, complex enterprises. Do legacy tools protect sufficiently against new and different vulnerabilities? If not, what constitutes a modern approach to DDoS protection, and why is it so crucial to business resilience?
The State of DDoS Attacks and Defense
DDoS attacks constitute a very significant and growing portion of the overall cybersecurity threat. In this post we recap highlights of a recent Webinar jointly presented by Kentik’s VP of Product Marketing, Alex Henthorn-Iwane, and Forrester Senior Analyst Joseph Blankenship. The Webinar focused on three areas: attack trends, the state of defense techniques, and key recommendations that organizations can implement to improve their protective posture.
Partnering with A10 Networks for DDoS Defense
While Kentik Detect’s ground-breaking DDoS detection is field-proven to catch 30% more attacks than legacy systems, our DDoS capabilities aren’t limited to standalone detection. We’re also actively working with leading mitigation providers to create end-to-end DDoS protection solutions. So we’re excited to be partnering with A10 Networks, whose products help defend some of the largest networks in the world, to enable seamless integration of Kentik Detect with A10 Thunder TPS mitigation.
Kentik CEO Avi Freedman with PacketPushers on NPM & DDoS
Avi Freedman recently spoke with Ethan Banks and Greg Ferro of PacketPushers about Kentik’s latest updates, which focus primarily on features that enhance network performance monitoring and DDoS protection. This post includes excerpts from that conversation as well as a link to the full podcast. Avi discusses his vision of appliance-free network monitoring, explains how host monitoring expands Kentik’s functionality, and gives an overview of how we detect and respond to anomalies and attacks.
How to Configure Remotely Triggered Black-Hole Routing with Kentik Detect
Destination-based Remotely Triggered Black-Hole routing (RTBH) is an incredibly effective and very cost-effective method of protecting your network during a DDoS attack. And with Kentik’s advanced Alerting system, automated RTBH is also relatively simple to configure. In this post, Kentik Customer Success Engineer Dan Rohan guides us through the process step by step.
How ISPs & Managed Service Providers Can Offer DDoS Protection
As organizations increasingly rely on digital operations there’s no end in sight to the DDoS epidemic. That aggravates the headaches for service providers, who stand between attackers and their targets, but it also creates the opportunity to offer effective protection services. Done right, these services can deepen customer relationships while expanding revenue and profits. But to succeed, providers will need to embrace big data as a key element of DDoS protection.
Big Data DDoS Protection vs the DDoS Marketplaces Threat
The source of DDoS attacks is typically depicted as a hoodie-wearing amateur. But the more serious threat is actually a well-developed marketplace for exploits, with vendors whose state-of-the-art technology can easily overwhelm legacy detection systems. In this post we look why you need the firepower of big data to fend off this new breed of commercial attackers.
The Dyn & Mirai Horror Show: The Weaponization of DDoS using Botnets
Whether its 70s variety shows or today’s DDoS attacks, high-profile success begets replication. So the recent attack on Dyn by Mirai-marshalled IoT botnets won’t be the last severe disruption of Internet access and commerce. Until infrastructure stakeholders come together around meaningful, enforceable standards for network protection, the security and prosperity of our connected world remains at risk.
Automate Remotely Triggered Black Hole DDoS Protection in Under an Hour
DDoS attacks pose a serious and growing threat, but traditional DDoS protection tools demand a plus-size capital budget. So many operators rely instead on manually-triggered RTBH, which is stressful, time-consuming, and error-prone. The solution is Kentik’S automated RTBH triggering, based on the industry’s most accurate DDoS detection, that sets up in under an hour with no hardware or software install.
How Scalable Architecture Boosts DDoS Detection Accuracy
Can legacy DDoS detection keep up with today’s attacks, or do inherent constraints limit network protection? In this post Jim Frey, Kentik VP Strategic Alliances, looks at how the limits of appliance-based detection systems contribute to inaccuracy — both false negatives and false positives — while the distributed big data architecture of Kentik Detect significantly enhances DDoS defense.
Avi Freedman Talks Attacks & Solutions: Cisco Live 2016
In our second post related to BrightTalk videos recorded with Kentik at Cisco Live 2016, Kentik CEO Avi Freedman talks about the increasing threats that digital businesses face from DDoS and other forms of attacks and service interruptions. Avi also discusses the attributes that are required or desirable in a network visibility solution in order to effectively protect a network.
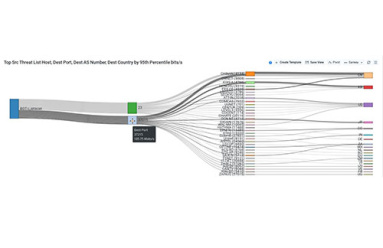
Exploring for Insights on Anomalous Network Traffic
By actively exploring network traffic with Kentik Detect you can reveal attacks and exploits that you haven’t already anticipated in your alerts. In previous posts we showed a range of techniques that help determine whether anomalous traffic indicates that a DDoS attack is underway. This time we dig deeper, gathering the actionable intelligence required to mitigate an attack without disrupting legitimate traffic.
Using Kentik Detect to Find Current Attacks
With massive data capacity and analytical flexibility, Kentik Detect makes it easy to actively explore network traffic. In this post we look at how to use this capability to rapidly discover and analyze interesting and potentially important DDoS and other attack vectors. We start with filtering by source geo, then zoom in on a time-span with anomalous traffic. By looking at unique source IPs and grouping traffic by destination IP we find both the source and the target of an attack.
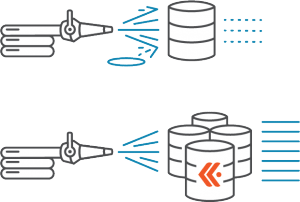
Transcending MySQL-Based NetFlow Analysis
For many of the organizations we’ve all worked with or known, SNMP gets dumped into RRDTool, and NetFlow is captured into MySQL. This arrangement is simple, well-documented, and works for initial requirements. But simply put, it’s not cost-effective to store flow data at any scale in a traditional relational database.