Understanding DDoS Attacks: Motivation and Impact

Summary
DDoS attacks disrupt services and damage reputations, with motivations ranging from political to personal. These attacks can also mask more severe security breaches, so early detection and mitigation are crucial. Learn how Kentik provides a solution by analyzing enriched NetFlow data to identify and mitigate DDoS threats.
There are many motivations for initiating a DDoS attack. Many are political, some are motivated by competition, and others are out of spite — such as disgruntled/former employees. Perpetrators can bring a target’s infrastructure to its knees, leveraging the situation to extort money, information, or apply negotiation pressure.
DDoS attacks are also used as a smoke-screen for other more insidious attacks, such as the introduction of malware or a more overt crime, like theft.
DDoS protection with network observability
Early detection and mitigation are critical for businesses that want to protect themselves against a DDoS attack. Some DDoS attacks are sophisticated enough to shut down large servers successfully and even completely disable a target’s network. This severe disruption to services and applications can result in direct revenue loss and damage to a brand’s reputation.
Let’s look at how Kentik can help networks detect, analyze, and mitigate DDoS attacks.

Low volume DDoS attacks
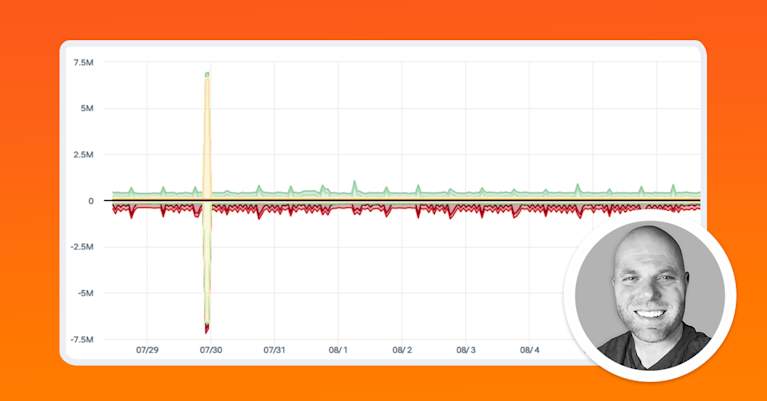
When most people think of DDoS attacks, they think of massive volumetric attacks that crash websites or networks. In reality, most DDoS attacks are small in size and duration, often less than 1 Gbps and only a few minutes long, making them difficult to detect. DDoS detection tools are often configured with detection thresholds that ignore or don’t see these attacks. These low-volume attacks are often used to mask security breaches. Hackers will use a DDoS attack to distract SecOps while simultaneously launching a more rewarding security breach. The security breach could involve exfiltrating data, mapping networks for vulnerabilities, or infiltrating ransomware.
Detection
Identifying where traffic originates, and normal traffic flows from those sources is keystone data to a defense strategy.
Kentik analyzes your real-time and historical NetFlow data, constantly comparing this traffic flow data against benchmarks to catch anomalous traffic patterns, giving network and security engineers what they need most: the awareness and time to mitigate the attack and protect their network before it does damage.
The solution allows you to baseline against small traffic volumes, and this way, your network engineers can fine-tune thresholds and alerts accordingly. The dynamic baseline function that uses machine learning to determine normal traffic is particularly powerful for low or slowly-growing traffic.
“In a DDoS attack you want to look at traffic volumes, but with Kentik we also can look at source IPs, AS numbers, and other metrics to see if it’s a distributed attack. This is so easy to do in Kentik; you simply add the source IP address dimension to the analysis.”
– Jurriën Rasing, Group Product Manager for Platform EngineeringPolicies
You can build policies based on specific geographies, such as an alert if the traffic is from an embargoed country. Being able to identify the source of the traffic can help tremendously in the detection of security breaches. Identifying traffic from an unusual source may be the key to early mitigation. Enriching the NetFlow data with network, geographical, and security context is the key to early detection.
Part of building the policies is to decide what action to take when the policy results in an alert. Is this a straightforward attack that needs immediate mitigation, or does this require human eyes on the data to decide what action to take?
DDoS Mitigation
You can mitigate a DDoS attack using several different methods. Two distinct groups of methods are supported for automation: the BGP native methods that remove all traffic and scrubbing.
“We were hesitant to consider a fully automated DDoS mitigation approach. Initially, we had team members approving each mitigation because we thought there would be false positives. After a few weeks with Kentik, we began to trust the detection completely, and full automation is now easy and essential for us. We no longer have to sit around waiting for the next attack to happen.”
– David Marble, President and CEOThe simplest BGP native method is remote triggered black hole (RTBH), where you redirect all traffic destined to the attacked IP space, be it a single address or a prefix, to a black hole where the packets are dropped and not forwarded.
Flowspec offers a much more granular removal of unwanted traffic. You can signal policies to the network edge and filter the unwanted traffic there based on the network context and details of the attack, like port numbers, protocols, source, destination, and more.
Hardware-based scrubbing requires hardware and methods to redirect traffic to the devices where the attack traffic is identified and removed inline, and the clean traffic forwarded to the attacked destination. Kentik’s powerful API is the foundation for integrations with A10 and Radware scrubbers and Cloudflare’s Magic Transit cloud-based scrubber. The RBTH and Flowspec functionality can be combined with the API to build custom integrations to other scrubbing platforms.
Understanding the attack in context
SNMP data is not enough!
Flow data gives you the ability to understand the attack in context. It details where the attack is coming from and what IP addresses, ports, or protocols make up the attack. The enriched NetFlow in the platform provides a deeper analysis. Dimensions like device, interface, geographical location of the attack sources, which network hosts the sources of the attack, and which providers bring the traffic to you.
This context helps with mitigation by being able to understand the nature of the attack better, as well as apply more accurate filters against the traffic.
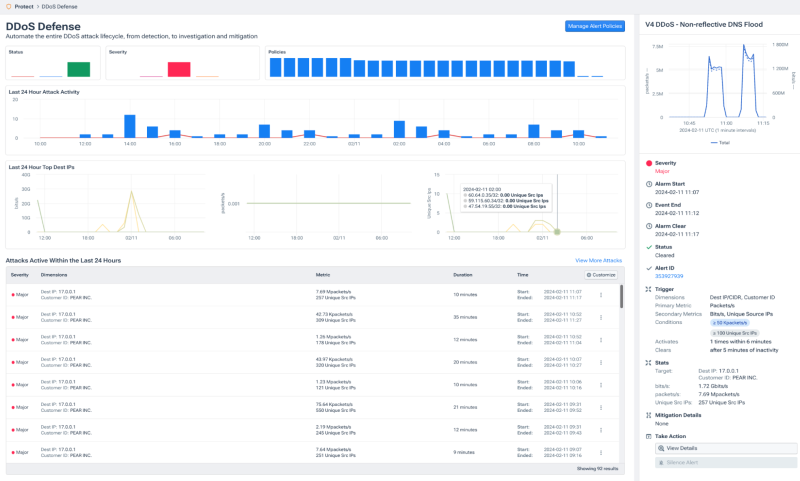
When you create the alerting policies, you decide what traffic you monitor. Any query made in Kentik Data Explorer can be the basis for an alert. There are several predefined policies available that can be used directly or customized.
From the alert overview or the DDoS workflow, there is quick access to visual and text information about what triggered an alert. From there, a deeper analysis is defined in the dashboards that are associated with the policy. This way, the experience of deep forensic analysis done either during or after an attack can be transformed into a predefined workflow for the next time this type of attack happens.
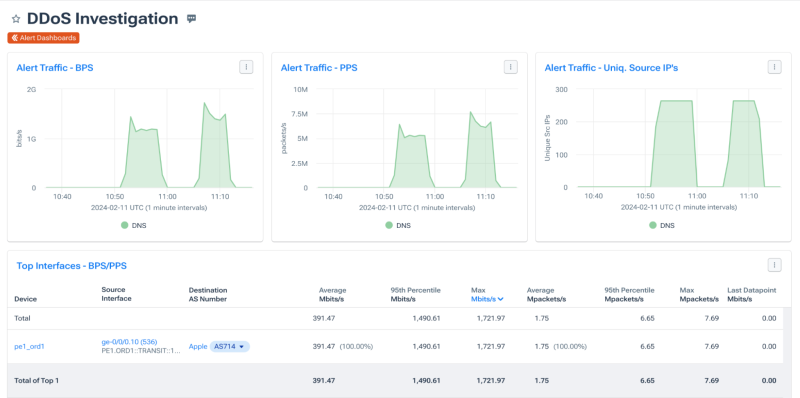
Determining the effectiveness of DDoS mitigation
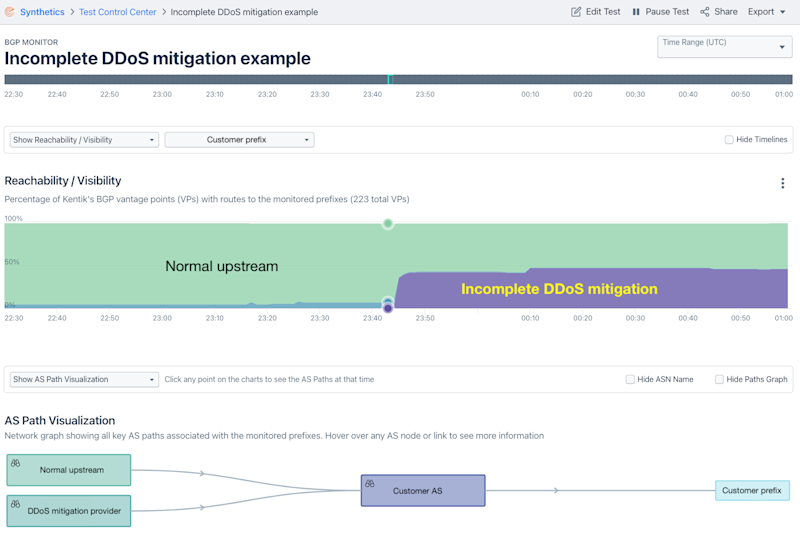
Mitigation services and technologies sometimes don’t achieve full coverage, and attack traffic can circumvent the mitigation, leaving you exposed. Using NetFlow to analyze what DDoS traffic has been redirected for scrubbing and what traffic has been missed is essential. And perhaps just as important, monitoring BGP from hundreds of vantage points can enable you to understand how quickly your mitigation service achieved full coverage, if it did at all.
The BGP visualization below shows a DDoS mitigation vendor (purple) appearing upstream of the customer network but never achieving complete coverage. Below, we can see the result of this incomplete activation, as only a portion of DDoS traffic is ultimately redirected to the DDoS mitigation vendor. An incomplete DDoS mitigation permits attack traffic to reach the target network, imperiling critical services.
Conclusion
DDoS attacks present a significant threat to businesses of all sizes, capable of disrupting services, tarnishing brand reputations, and incurring substantial financial losses. As these attacks evolve in complexity and intensity, the need for advanced, comprehensive defense strategies becomes imperative. Kentik emerges as a powerful ally in this ongoing battle, offering a robust suite of tools for early detection, granular analysis, and effective mitigation of DDoS threats.
Through its sophisticated analysis of NetFlow data, enriched with network, geographical, and security context, Kentik provides unparalleled visibility into network traffic. This enables businesses to detect and mitigate attacks in their infancy and understand the nature of these threats in a broader context. With capabilities ranging from detecting subtle, low-volume attacks to deploying advanced mitigation techniques like BGP Flowspec and hardware-based scrubbing, Kentik equips network and security engineers with the resources they need to protect their infrastructure.