BGP Flowspec Doesn't Suck. We're Just Using it Wrong.

Summary
BGP Flowspec is one of the critical technologies gaining traction in DDoS mitigation strategies. In this article, Justin Ryburn outlines the adoption rates and best practices of this emerging and effective DDoS mitigation tool.
Introduction
DDoS attacks continue to plague the internet, posing a persistent threat to businesses of all sizes. As attackers evolve their tactics, our defenses must adapt to mitigate these threats effectively. A DDoS attack can cause significant issues for customers and can be very time-consuming for network operators to track down and stop. Those who have followed me for a while may be aware I am a big proponent of BGP Flowspec. I’ve done public speaking on the topic and even published a short book, A Day One Guide, detailing how to configure it on Juniper devices. I truly believe that BGP Flowspec can be a big help to operators in blocking these attacks. Like most things in IT, it does not come without drawbacks and must be implemented properly. In this blog, I’ll give a refresher on BGP Flowspec and why I believe more operators should test and adopt the technology.
DDoS trends
Recent industry reports from leading cybersecurity firms such as Akamai and Cloudflare provide a picture of the ongoing battle against DDoS attacks. According to Akamai’s retrospective on DDoS trends in 2023 and Cloudflare’s DDoS threat report for 2023 Q4, the frequency and complexity of DDoS attacks continue to rise, driving more organizations towards cloud-based mitigation services while moving away from traditional appliance-based solutions.
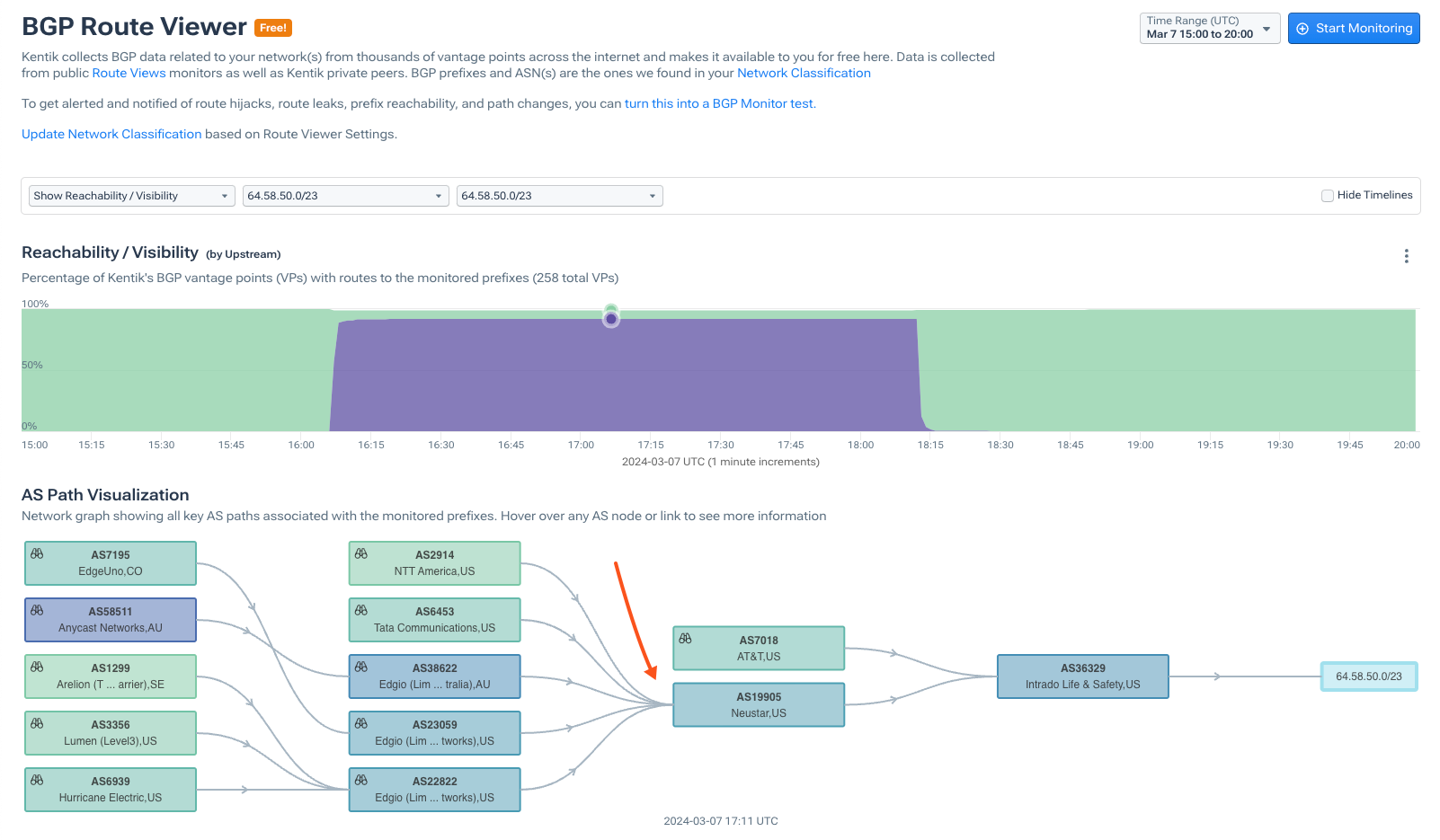
One of the cool things about working for a network observability company that analyzes the global BGP table is that we can see when an organization activates a cloud-based scrubbing service by looking at the changes in the BGP table. In this visualization, you can see Intrado Life & Safety (ASN 36329), which uses AT&T (ASN 7018) as its upstream provider. When they are under attack, they swing their traffic over to Neustar (ASN 19905) to mitigate it.
An effective BGP configuration is pivotal to controlling your organization’s destiny on the internet. Learn the basics and evolution of BGP.

BGP Flowspec: A powerful tool
One of the key technologies gaining traction in DDoS mitigation strategies is BGP Flowspec. Before we delve into its adoption rates and best practices, let’s have a quick refresher on how BGP Flowspec works. BGP Flowspec adds a new NLRI (Network Layer Reachability Information) that allows the operator to specify very detailed parameters for the type of attack they wish to mitigate. Here is a list of the possible parameters that can be specified:
Type 1 - Destination prefix
Type 2 - Source prefix
Type 3 - IP protocol
Type 4 - Port
Type 5 - Destination port
Type 6 - Source port
Type 7 - ICMP type
Type 8 - ICMP code
Type 9 - TCP flags
Type 10 - Packet length
Type 11 - DSCP (Diffserv Code Point)
Type 12 - Fragment
Once you have signaled what traffic you want to match on, you must tell the router what to do with that traffic. This is done by attaching extended communities to the announced BGP NLRI. Here is a table of those options:
| Type | Extended Community | Encoding |
|---|---|---|
| 0x8006 | traffic-rate | 2-byte as#, 4-byte float |
| 0x8007 | traffic-action | bitmask |
| 0x8008 | redirect | 6-byte Route Target |
| 0x8009 | traffic-marking | DSCP value |
For more details, check out the IETF’s RFC 8955.
Adoption rates
While BGP Flowspec holds immense potential for mitigating DDoS attacks, its adoption rates vary across organizations. It’s 2024, so of course, we are going to ask ChatGPT what it knows about BGP Flowspec adoption rates:
All joking aside, it is hard to get good data on the adoption rates as most organizations just go about doing it quietly. There has not been much research on which networks have it enabled in their own network. I talk to a lot of customers who are either using it or in the process of testing it in their lab before deployment. My limited data set would indicate that interest and adoption is growing. Adoption rates are lower than many would have hoped when the IETF ratified RFC 5575 (which RFC 8955 replaced) years ago.
Best practices for safe adoption
Like any powerful technology, BGP Flowspec can have adverse outcomes if deployed incorrectly. BGP Flowspec as a protocol has a negative impression in the minds of many network engineers due to some very public outages caused by its misuse. The two most famous were the 2020 CenturyLink outage and the 2013 Cloudflare outage.
However, this should not deter organizations from leveraging its capabilities in a careful and well-thought-out manner. To ensure safe adoption, it’s essential to follow best practices such as thorough testing, ongoing monitoring, and adjustment of deployment policies.
I advise customers to test forwarding performance with different BGP Flowspec rules deployed carefully. Most line card ASICs that I am aware of have a finite amount of resources they can allocate to this filter. As the number of prefixes increases, those resources get used up, and the ASICs can no longer forward packets at line rate. Also, not all FS rules are created equally. The more complex the matching criteria, the more resources it is going to take on the ASIC.
The next thing to be aware of is the filtering that is done as a result of processing the BGP Flowspec rules, which takes place as a forwarding table filter. What that means is it applies to all the interfaces on the device. Some vendors allow configurations to exclude specific interfaces like backbone links, out-of-band management interfaces, etc. This may be something that you want to consider to make sure you do not lose access to the device when the filter is applied.
My final recommendation is to have tight control over what kind of BGP Flowspec rules you allow your system to advertise to your routes. The Cloudflare outage I mentioned earlier resulted from them advertising a rule that blocked packets between 99,971 and 99,985 bytes long. As you probably know, those packet sizes do not make sense, as most networks have a maximum packet size of ~9,000 bytes. This caused their Juniper line cards to panic and drop all traffic. The router should not have reacted that way, but Cloudflare should have also had checks in their automation platform to sanity check for packet size being in a reasonable range.
Staying current
Keeping abreast of the latest developments in BGP Flowspec is crucial for effective DDoS mitigation strategies. Stay informed about the latest updates from the Internet Engineering Task Force (IETF) regarding BGP Flowspec standards and implementations. BGP Flowspec is maintained by the Inter-Domain Routing Group (IDR), and you can follow their mailing list here. Ultimately, BGP Flowspec offers a potent solution to combat DDoS attacks, and it’s up to us as operators to harness its power responsibly.
In conclusion, while DDoS attacks continue to pose significant challenges, solutions like BGP Flowspec provide hope for organizations seeking robust defense mechanisms. By understanding its capabilities, adopting best practices, and staying informed about industry developments, we can collectively strengthen our resilience against the ever-evolving threat landscape of DDoS attacks. As I said earlier, I am a big proponent of BGP Flowspec. If you are considering deploying it and have questions, feel free to reach out to me, and I will be happy to answer any questions I can.



