Dissecting the FCC’s Proposal to Improve BGP Security

Summary
The FCC recently published a proposal to require nine major US internet service providers to deploy RPKI Route Origin Validation (ROV). In this post, we’ll look at the proposal and where the nine service providers currently stand with respect to ROV.
As part of its ongoing efforts to improve Border Gateway Protocol (BGP) routing security, the US Federal Communications Commission (FCC) proposed a rule last month that it hoped would “increase the security of the information routed across the internet and promote national security.”
Specifically, the FCC is seeking comment on a proposal that would require nine major US internet service providers to draft “BGP Routing Security Risk Management Plans” (BGP Plans), and confidentially report them to the federal agency.
These “BGP Plans” would primarily cover two areas:
- Describe the specific efforts made to create and maintain Route Origin Authorizations (ROAs) for at least 90% of the routes under its control. [¶ 37, 54]
- Describe the extent to which it has implemented ROV filtering at its interconnection points. [¶ 50]
In other words, each provider would report its progress deploying RPKI Route Origin Validation (ROV).

In this blog post, we’ll take a look at each of these nine service providers and see where they stand with respect to ROA creation using Kentik’s unique data sets.
Background
In her remarks on the proposal, Chairwoman Jessica Rosenworcel summed up the importance of securing internet routing like this:
…we all rely on BGP. Every one of us, every day. That is true if you are running a small business and using connections to engage with customers and suppliers, banking online, having a telemedicine session with a healthcare provider, helping the kids with their digital age schoolwork, staying in touch with family, or keeping up to date on the news. BGP is in the background, helping connect our critical infrastructure, support emergency services, keep the financial sector running, shore up manufacturing, and more.
In February 2022, the FCC began its work on this important topic by launching an inquiry seeking comment on the best ways to help address BGP security.
In July 2023, the FCC hosted a workshop on BGP security in which multiple presenters cited Kentik’s analysis on RPKI ROV adoption. Tony Tauber, Engineering Fellow at Comcast, cited our analysis to argue that traffic data (i.e., NetFlow) suggests that we’re farther along in RPKI ROV adoption than the raw counts of BGP routes might suggest. Nimrod Levy of AT&T cited our observation that a route that is evaluated as RPKI-invalid will have its propagation reduced by 50% or more.
And last summer, Chairwoman Rosenworcel and Jen Easterly, Director of the Cybersecurity and Infrastructure Security Agency (CISA), co-published a call to action on BGP security entitled, The Most Important Part of the Internet You’ve Probably Never Heard Of. Although, If you’re reading this post, I’m going to guess you’ve probably heard of it. 😀
The full FCC proposal cites analysis from Kentik on multiple occasions throughout the document. Paragraph 4 cites my post, A Brief History of the Internet’s Biggest BGP Incidents, to help describe the vulnerabilities present in our current internet routing system. Paragraph 11 cites our post, What can be learned from recent BGP hijacks targeting cryptocurrency services?, which covered how BGP hijacks were successfully employed by hackers against cryptocurrency services. Finally, paragraph 18 cites Exploring the Latest RPKI ROV Adoption Numbers, which was part of my continuing collaboration with Job Snijders of Fastly to measure RPKI ROV adoption.
Internet Society and Global Cyber Alliance response
In reaction to the proposed FCC rule, the Internet Society joined with the Global Cyber Alliance (the former and current homes of the MANRS secure routing initiative) to publish an Ex Parte response pushing back on any attempt to regulate BGP.
They argue that codifying a technical security mechanism would be counterproductive. The first piece of this argument states that “the United States industry is already addressing routing security challenges,” and to support this claim, the paper relies on my collaboration with Job on both progress on ROA creation as well as the rejection of RPKI-invalids.
The Ex Parte goes on to argue that regulations could limit the ability of service providers to quickly adapt to emerging security standards and could prove burdensome for smaller service providers. If security standards change in the future, the paper argues, regulation could hinder the ability of service providers to quickly adapt. Job Snijders raised similar points in his 2022 FCC filing.
The nine
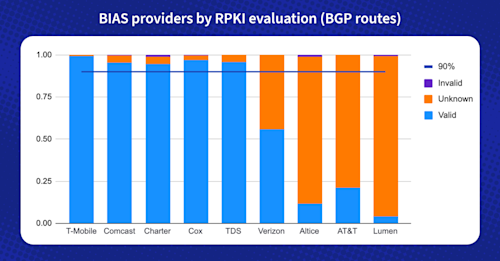
The proposal focuses on providers of “broadband internet access service (BIAS).” Let’s see where these companies presently stand in terms of both BGP routes and traffic statistics based on Kentik’s aggregate NetFlow data.
For each of the nine service providers below, I discuss the ASNs we’re using for the analysis, the percentage of routes originated by those ASNs that have ROAs, and, finally, the proportion of traffic going to those routes versus routes without ROAs.
AT&T
ASNs: 7018, 20057
While AT&T has over 100 ASNs, Kentik’s traffic statistics reveal that 98% of traffic to AT&T goes to AS7018 and AS20057. In order to simplify our analysis, we’ll just use those two ASNs. At the beginning of July 2024, we observed AS7018 as originating 2995 prefixes in total. 960 of those were RPKI-valid, while 2034 were RPKI-unknown. AS20057 originates 1537 prefixes and none of them have ROAs.
Kentik observes that 58.1% of traffic in bits/sec to AT&T is to RPKI-valid routes, while the rest goes to routes without ROAs.
- Routes with ROAs: 21.2%
- Proportion of traffic: 58.1%
Altice
ASNs: 19108 and 6128
Altice is a European telecommunications conglomerate. For this analysis, we’ll use their US networks, AS19108 (the former Suddenlink) and AS6128 (Cablevision). As of this writing, 68 of the 95 routes originated by AS6128 are RPKI-valid, while only 25 prefixes are RPKI-valid out of the 694 routes originated by AS19108.
Based on Kentik’s statistics, virtually all traffic destined for AS6128 was to routes with ROAs, while all of the traffic to AS19108 was to routes without ROAs. Therefore, the proportion of traffic to routes with ROAs is reflective of the breakdown to traffic terminating in these two ASNs, as seen in our aggregate NetFlow. AS6128 also originates a few RPKI-invalid routes, such as 66.152.159.0/24.
- Routes with ROAs: 11.8%
- Proportion of traffic: 60.6%
Charter/Spectrum
ASNs: 20115, 20001, 11427, 10796, 33363 and 20+ more
Charter, which goes by the trade name of Spectrum, is composed of several acquisitions, including Time Warner Cable. Whether counting cumulative BGP routes or aggregate traffic volume, Charter presently scores very high in terms of RPKI ROV deployment.
- Routes with ROAs: 92.6%
- Proportion of traffic: 99.9%
Comcast
ASNs 7922 and 20+ more
Like AT&T, Comcast uses numerous ASNs. We’ve included the top 29 Comcast ASNs based on traffic in this analysis. By either metric (BGP routes or traffic), Comcast scores very high in terms of RPKI ROV preparedness.
The Comcast ASNs in our analysis originated 4583 prefixes, 4362 (93.5%) of which had ROAs. In addition, we see 99.4% of traffic to these Comcast ASNs going to these routes with ROAs.
- Routes with ROAs: 93.5%
- Proportion of traffic: 99.4%
Cox
ASN: 22773
AS22773 originates 4,845 prefixes, 96.97% of which are RPKI-valid. AS22773 also announces a handful of RPKI-invalid routes, such as 50.118.213.0/24. Based on Kentik’s statistics, 98.2% of traffic to Cox goes to RPKI-valid routes.
- Routes with ROAs: 96.7%
- Proportion of traffic: 99.8%
Lumen
ASNs: 3356, 209, 3561, 22561
Lumen might not be a household name outside of places like Seattle* but it plays an important role for the global internet. It is unlike nearly any other service provider on this list because of its additional role as one of the world’s largest transit providers.
Composed of the networks of acquired telecommunications companies, including Qwest (AS209), Level 3 (AS3356), and Savvis (AS3561), Lumen is one of the largest telecommunications providers in the United States.
According to Kentik’s statistics, most traffic to Lumen is destined for the networks of AS209 and AS3356, and nearly none of the prefixes originated by Lumen’s ASNs have ROAs. However, it should be emphasized that AS209 and AS3356 reject RPKI-invalid routes, providing a critical benefit to their large international customer base and the greater internet. Now, they need to begin creating ROAs.
- Routes with ROAs: 3.9%
- Proportion of traffic: 0.0%
*Lumen Field is the home stadium of the Seattle Seahawks of the NFL, Seattle Sounders FC of the MLS, and Seattle Reign FC of the National Women’s Soccer League.
T-Mobile
ASN: 21928
As far as RPKI ROV preparedness goes, T-Mobile is clearly the best of the US mobile providers. This is likely due to the fact that T-Mobile’s business is entirely providing mobile service while the other US operators provide a variety of other network services, some of which were gained through prior acquisitions.
Regardless, 99.2% of the 528 routes originated by AS21928 have ROAs, and virtually all traffic to T-Mobile is destined for IP space covered by ROAs.
- Routes with ROAs: 99.2%
- Proportion of traffic: 100%
TDS
ASNs: 4181, 6614
In this analysis, we used two ASNs to represent TDS: AS4181 (TDS) and AS6614 (US Cellular). These two networks are polar opposites when it comes to RPKI ROV deployment.
AS4181 has ROAs for virtually all of the 1200+ routes it originates, and the proportion of traffic to AS4181 routes with ROAs is 100%. Conversely, AS6614 has ROAs for none of the 53 routes it originates.
Since US Cellular is in the process of being sold to T-Mobile (listed above), AS6614 will soon be part of that network, and it will be the acquirer’s responsibility to deploy RPKI ROV on the network. The FCC proposal explicitly mentioned that US Cellular should be counted as part of TDS, despite the pending sale. If we removed AS6614 from the analysis, TDS would have nearly perfect coverage as measured by both BGP routes and traffic stats.
- Routes with ROAs: 95.6%
- Proportion of traffic: 82.5%
Verizon
ASNs: 701, 6167, 22394
For this analysis, we used AS701, AS6167, and AS22394 to represent Verizon’s mobile service in the US. AS702 and AS703 are also part of Verizon, but they provide service in EMEA and Asia-Pacific, respectively, and are therefore out of scope.
Based on Kentik’s aggregate NetFlow data, AS701 is the biggest destination of traffic to Verizon in the US. A clear majority (819 out of 1044) of the routes originated by AS701 have ROAs, and 76.3% of the traffic to AS701 goes to routes with ROAs.
A little under half of the routes originated by AS6167 have ROAs and only a sixth of those originated by AS22394.
- Routes with ROAs: 56%
- Proportion of traffic: 64.1%
Summary of analysis
Based on the analysis described above, only five of the nine BIAS providers named in the FCC proposal would currently pass the 90% metric of routes with ROAs. Of course, this metric could be gamed by providers who could de-aggregate (i.e., split into more routes) address space covered by ROAs and aggregate routes (i.e., consolidate into fewer routes) containing address space not covered by ROAs.
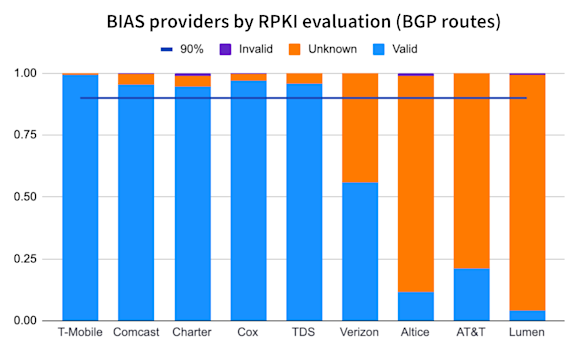
Regardless, the other four providers have some work to do here to receive a passing grade.
Of course, the BGP plans the FCC is asking for are “risk management“ plans. One way to focus on this risk is to not treat each BGP route equally but instead focus on where traffic is going. Some routes simply don’t carry much traffic at all and therefore pose less risk.
Kentik’s aggregate NetFlow enables us to uniquely operate in this dimension. Below is the same set of providers named in the proposal when traffic volume (bits/sec) are used as a metric instead of counts of BGP routes. It would also be more difficult for a provider to game this metric than counts of BGP routes. On the other hand, it would not capture the importance of routes which contain critical, but low traffic services such as DNS.
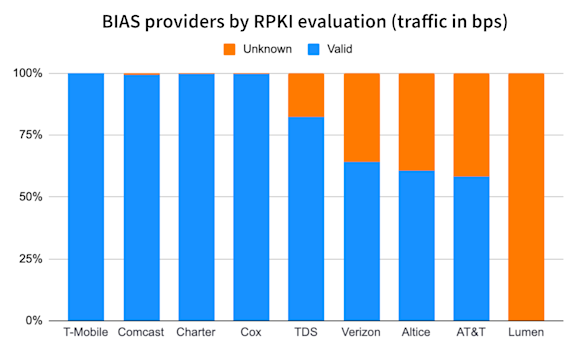
TDS has a lower percentage of “valid traffic” simply due to the inclusion of US Cellular which has no ROAs for its IP address space. Verizon, Altice and AT&T all appear much more favorable when traffic is analyzed, as opposed to counts of BGP routes. These providers may have already conducted some risk management and focused their RPKI deployment efforts on the more important routes. Lumen is low in both metrics.
Conclusion
It is unclear if requiring the deployment of RPKI ROV is the right move. Such a requirement may not be necessary and have unintended consequences. As the Ex Parte response from ISOC and GCA points out, the US government (to include the US Department of Defense) is lightyears behind most major US service providers in terms of RPKI ROV deployment. Perhaps the FCC could begin with the networks of the US federal government before requiring the same of private industry.
It’s also important to appreciate how we were able to make significant progress on deploying this technology. A couple of months ago, we broke the 50% barrier for IPv4 routes with ROAs. This global feat was accomplished without government mandates. It took years of technical discussions, debate, and advocacy until it became “socially unacceptable” within the internet community to not have a plan for RPKI ROV. Peer pressure and, frankly, shame, can be powerful motivators.
Lastly, it will be interesting to see how the recent Supreme Court decision to overturn the long-standing Chevron deference in Loper Bright Enterprises v. Raimondo affects the FCC’s ability to develop rules such as this one. If the development of such a rule requires an act of Congress, it may be unlikely to ever happen.
Thankfully, the internet community has shown that progress is possible without regulatory requirements. Good thing, because securing BGP routing is going to take a lot more than just the widespread deployment of RPKI ROV, as great as it is.
We need to continue to work together to develop and advocate for additional mechanisms of route hygiene, and there are many ways the FCC can play a vital role in those efforts. These include providing grants to those developing the software needed to enable routing security or by collecting and disseminating adoption metrics like the ones presented in this blog post.
If you wish to contribute your opinion or expertise on this topic, you can do so by submitting a filing here.