How to Achieve Multi-Cloud Visibility in Hybrid and Multi-Cloud Architectures

Summary
Learn how to maintain multi-cloud visibility within hybrid and multi-cloud architectures, as well as the requirements for modern cloud monitoring tools.
Multi-cloud is quickly becoming a “new normal” deployment scenario as organizations of all types leverage an ever-increasing variety of cloud computing services. Here are just four of the reasons for this trend:
- Preference: Different teams within an organization have different preferences when picking clouds due to each team’s competency and specialization.
- No lock-in: The move to multi-cloud avoids vendor “lock-in” and reduces reliance on one cloud provider. This helps many organizations not only gain stronger negotiating power but also build a more resilient infrastructure.
- Efficiency: Multi-cloud can promote operational efficiency that generates positive business outcomes (e.g., enabling rapid migration when pricing or capability make it appealing).
- Regulations: Some make a move to meet compliance/regulatory requirements for international business.
Regardless of the exact “whys,” adoption of cloud architectures doesn’t happen in a vacuum. Many cloud services are deployed to extend, supplement, or enhance existing on-prem infrastructure. And so, whenever we talk about “multi-cloud” architectures, we should also consider “hybrid-cloud” architectures — these two scenarios go hand-in-hand when we take a holistic look at an organization’s network infrastructure.
Understanding Multi-Cloud and Hybrid Cloud Architectures
As multi-cloud adoption becomes more prevalent, it’s essential to understand both multi-cloud and hybrid-cloud architectures. At a basic level, these models determine how cloud resources interact and integrate with each other and potentially with on-premises infrastructure.
What is Multi-Cloud Architecture?
In a multi-cloud architecture, an organization uses multiple cloud providers to fulfill its computing needs. It’s not about redundancy; different cloud providers are often chosen because they excel in particular service offerings or workloads. For example, one provider might offer optimal database services while another has a superior machine learning platform. By employing a multi-cloud strategy, organizations can harness the strengths of various providers, ensuring operational efficiency and avoiding a one-size-fits-all approach.
What is Hybrid Cloud Architecture?
On the other hand, a hybrid cloud architecture blends the use of public cloud resources with on-premises infrastructure. This setup offers organizations the flexibility of the cloud while retaining the control and security of their on-premises systems. The hybrid approach’s key advantages include deployment flexibility, better data control, and the ability to scale out (using public cloud) without major changes to existing on-prem setups.
What is Multi-Cloud Visibility and Why is it Important?
In multi-cloud architectures, visibility is not just about seeing your resources but understanding how they interact across diverse environments.
Effective management of multi-cloud environments demands a comprehensive view across all cloud providers and on-prem infrastructures. With multiple clouds, each with its unique dashboard and metrics, it can be a Herculean task to maintain a cohesive picture of operations. Moreover, monitoring dispersed resources and workloads becomes increasingly complex due to the sheer volume of data and the potential for disparities.
However, a unified view becomes indispensable in ensuring optimal performance. Potential issues like latency, data transfer bottlenecks, or inconsistencies can arise as resources spread across multiple providers. Comprehensive multi-cloud visibility allows organizations to address these concerns preemptively, ensuring seamless operations and the high performance that today’s digital enterprises demand.
The Reality of Multi-Cloud Visibility Today
Along with the rise of hybrid- and multi-cloud architectures, it’s worth noting another reality — visibility (or lack thereof). In multi-cloud environments, it’s no longer sufficient to leverage each cloud provider’s built-in visibility tools. Those tools were built for each provider’s own cloud infrastructure, and they typically lack some essential features, including:
- Resiliency: The built-in cloud monitoring tools for an IaaS solution reside inside that public cloud! When that provider’s cloud service goes down, its native monitoring services will also be impacted. Users can no longer rely on built-in monitoring tools to do any kind of troubleshooting in such a scenario and will be left in the dark.
- Lack of a holistic view across multiple cloud providers and the organization’s on-prem infrastructure. For example, you cannot use AWS CloudWatch to monitor GCP’s network statistics and/or your on-prem data centers. Today, there remains a huge gap between the need for a unified view (one that allows monitoring of your entire infrastructure in hybrid/multi-cloud environments) and the tools that are available within each environment.
- An individual cloud vendor is probably not the Subject Matter Expert you want for all of your networks, old and new (including the ones you own).
The Need for a Modern Cloud Monitoring Tool
In hybrid and multi-cloud environments, a modern monitoring tool should meet four key requirements:
- Unified view: A modern cloud monitoring tool must provide a unified view across your entire infrastructure — hybrid, multi-cloud, and on-premise components. A single-pane-of-glass view and management can help reduce operational complexities and avoid silos.
- Powerful analytics: The tool must unlock powerful analytics and enable in-depth visibility. The tool must also be able to help manage the top challenges we face with modern cloud infrastructures, including performance, cost, and security. Analytics features should be contextualized and enable you to answer both technical and business questions for various stakeholders.
- Modern integrations: Such a tool must also integrate with container orchestration and service mesh management (e.g., Istio). One major cloud advantage is the agility of adopting cloud-native architecture, including containers/microservices. However, to leverage that advantage, your monitoring tool needs to provide visibility into the communications between those services (e.g., when the communication between them is slow, that means business is at risk).
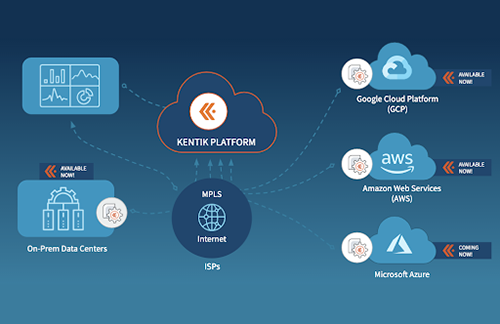
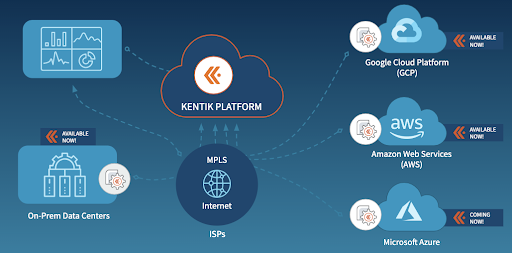
Kentik for Multi-Cloud Visibility: Now with Support for GCP, AWS and Microsoft Azure Flows
Kentik is on a fast and firm pace to expand cloud visibility for on-prem to public clouds. We are on a mission to provide a scalable, powerful, and easy-to-use__ solution that provides holistic and unified insights for your infrastructure.
Last summer, we started with a Google Cloud Platform (GCP) integration by adding GCP VPC Flow Logs as one of the data sources (see our GCP VPC Flow Logs blog post and GCP solution brief for more detail). Last winter, we enabled visibility into AWS with its VPC Flow Logs (see our AWS Visibility blog post and AWS visibility solution brief).
But we haven’t stopped there: Now, as of spring 2019, we put our footprint into Azure by integrating Network Security Group Version 2 (NSGv2) Flow Logs as well. For more detail, read our new solution brief about Azure NSG Flow Logs for Kentik.
Getting Started with the Azure NSGv2 Flow Logs Integration
Azure NSGv2 Flow Logs allow you to get information about ingress and egress IP traffic through a Network Security Group (NSG) on a per-rule basis.
The onboarding workflow is straightforward. To export Azure NSGv2 Flow Logs to the Kentik platform, just follow these few steps:
- Gather Azure Information: This might include Azure Role, Azure Subscription ID, Resource Group and Location from your Azure instance. The main goal is to make sure that you have the essential information handy and have the right permissions granted for the exporting.
- Add Azure Cloud and Complete the Settings:

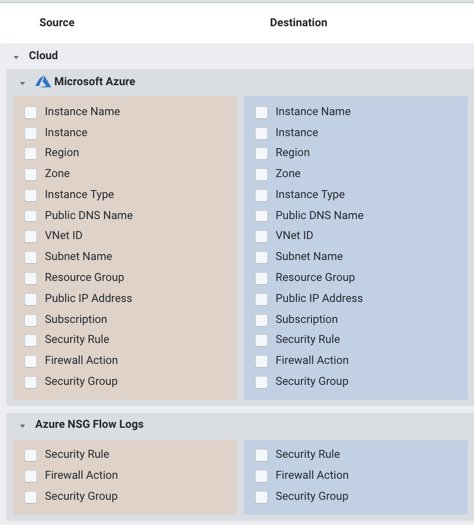
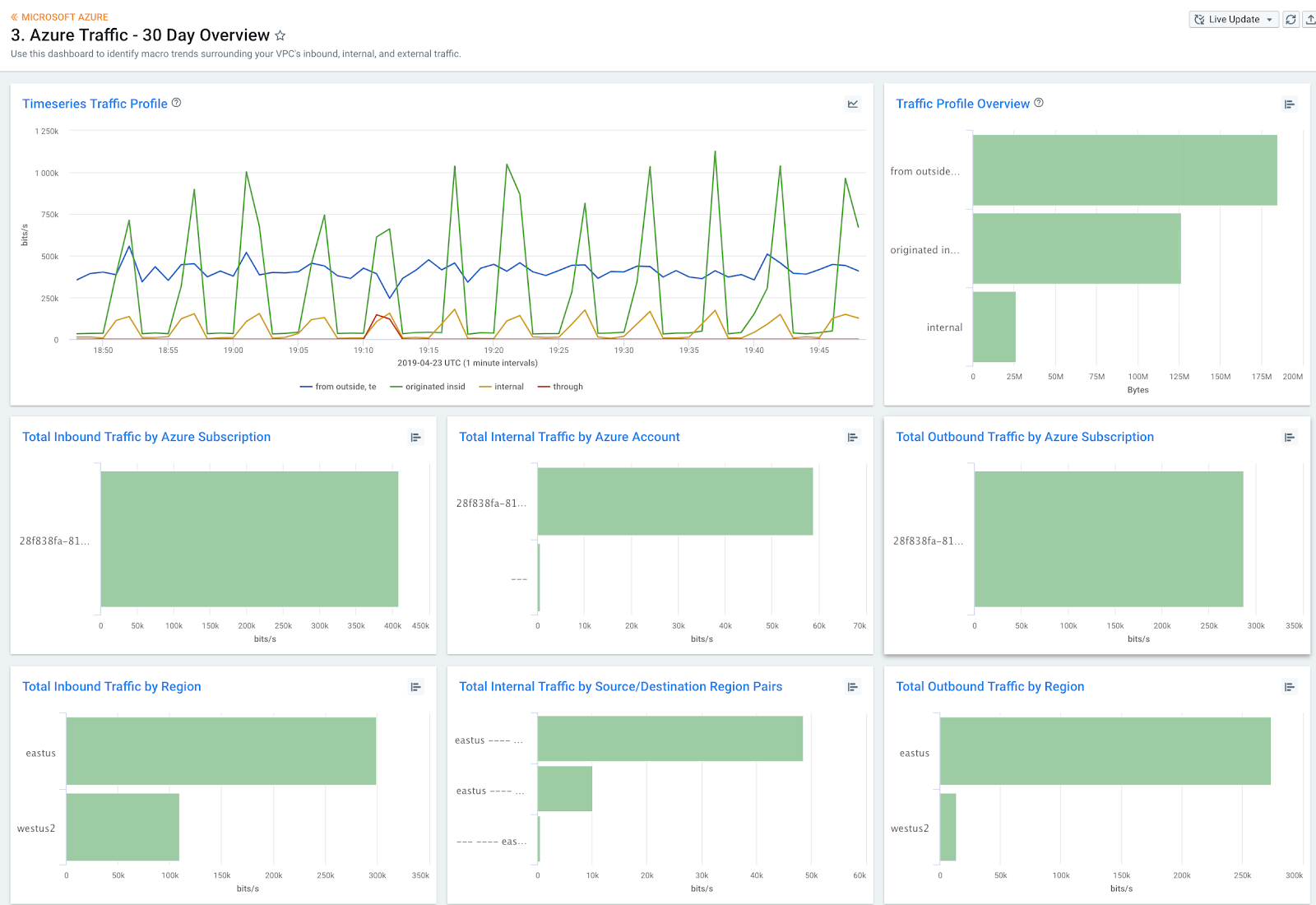
Kentik for Multi-Cloud: AWS + Azure + GCP
The Azure integration completes Kentik’s trifecta of public cloud options. Kentik’s cloud visibility platform now provides easy analytics, powerful visualization, and instant insight, empowering customers with:
- A unified view across hybrid and multi-cloud into your infrastructure
- Integrated with container orchestration and service mesh management
- The ability to manage performance, cost, and security issues across modern cloud infrastructures
For more information on how to leverage the traffic data from your infrastructure and put it into application and business context for your hybrid and multi-cloud environment, you can read our cloud visibility solution brief, request a personalized demonstration, or sign up for a free trial.