Summary
On March 18, 2025, North Korea’s BGP routes became RPKI-invalid due to the publication of a faulty ROA. In this post, we’ll visualize the impact on the propagation of affected routes and what North Korea (and you too!) can do to avoid problems with the optional maxLength attribute.
At 09:30:15 UTC on Tuesday, March 18, APNIC signed a new Route Origin Authorization (ROA) for a country that had never had one before: North Korea. However, as was first reported by the North Korean Internet blog, there was a problem.
The new ROA specified a maximum prefix length of 22, shorter than the four /24 routes originated by North Korea’s only ISP, Star JV (AS131279), rendering the routes RPKI-invalid. As such, minutes after the publication of this problematic ROA, many international carriers began rejecting routes from the modern-day hermit kingdom, dramatically reducing their propagation and the country’s reachability from the internet.
Impacts on route propagation
Let’s take a look at what the introduction of the faulty ROA did to the reachability of two of the four North Korean routes.
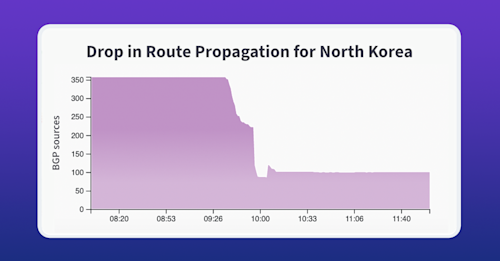
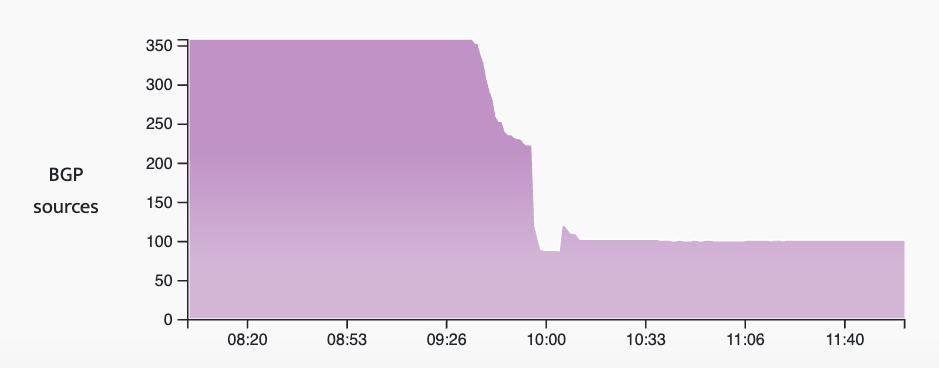
175.45.176.0/24 is originated by AS131279, passed exclusively to AS134544 (Cenbong Holdings), China Unicom (AS4837), and on to a slew of international carriers and peers of China Unicom. The graphic below shows how many Routeviews BGP sources had this route in their tables over time. There is a clear dropoff beginning at 09:36 UTC, accelerating downwards until it stabilizes at around 100 sources (aka vantage points).
If we expand the view to break down how the internet (we’ll use Routeviews BGP sources as a stand-in) reached AS4837 to get to 175.45.176.0/24 over time, we arrive at the visualization below. The colors reveal how different carriers drop the route (or not!) over time and how that contributes to the overall decline in propagation.

Specifically, Arelion (AS1299) in pink is the first to go, taking with it almost a hundred sources. GTT (AS3257, yellow) and Verizon (AS701, cyan) go soon after. Cogent (AS174, orange) briefly emerges as a popular path until its systems catch up and blot the RPKI-invalid routes out of its tables. Conversely, AS6762, AS6939, and AS5511 never stop carrying the route.
For another view, let’s take a look at the propagation of 175.45.177.0/24. Like the previous example, things start coming undone around 09:36 UTC when the propagation declines more severely and in a noticeably different shape.

The difference for 175.45.177.0/24 is due to how it is transited. Back in October 2017, I, along with North Korea technology expert Martyn Williams, broke the story of the emergence of the first non-Chinese internet link for North Korea. The new connection to the global internet was run over the Korea-Russia Friendship Bridge, connecting North Korea to Russia.
Given the Korea-Russia bridge is a rail crossing, it is perhaps not surprising that the Russian provider TransTeleCom (aka TTK, AS20485) emerged as AS131279’s new Russian transit provider. TTK is a national backbone operator in Russia that was built using fiber optic lines run along the country’s rail system.
In sum, the internet exclusively uses China to reach 175.45.176.0/24, and it exclusively uses Russia to reach 175.45.177.0/24. Hence, the difference in the changes in propagation.
If we expand the visualization for 175.45.177.0/24 like we did last time, we can see what happened to the upstreams of AS20485 when the route became RPKI-invalid. The biggest initial change is the loss of PCCW (tan, AS3491) and Zayo (dark grey, AS6461), with Cogent (orange, AS174) the last to go.
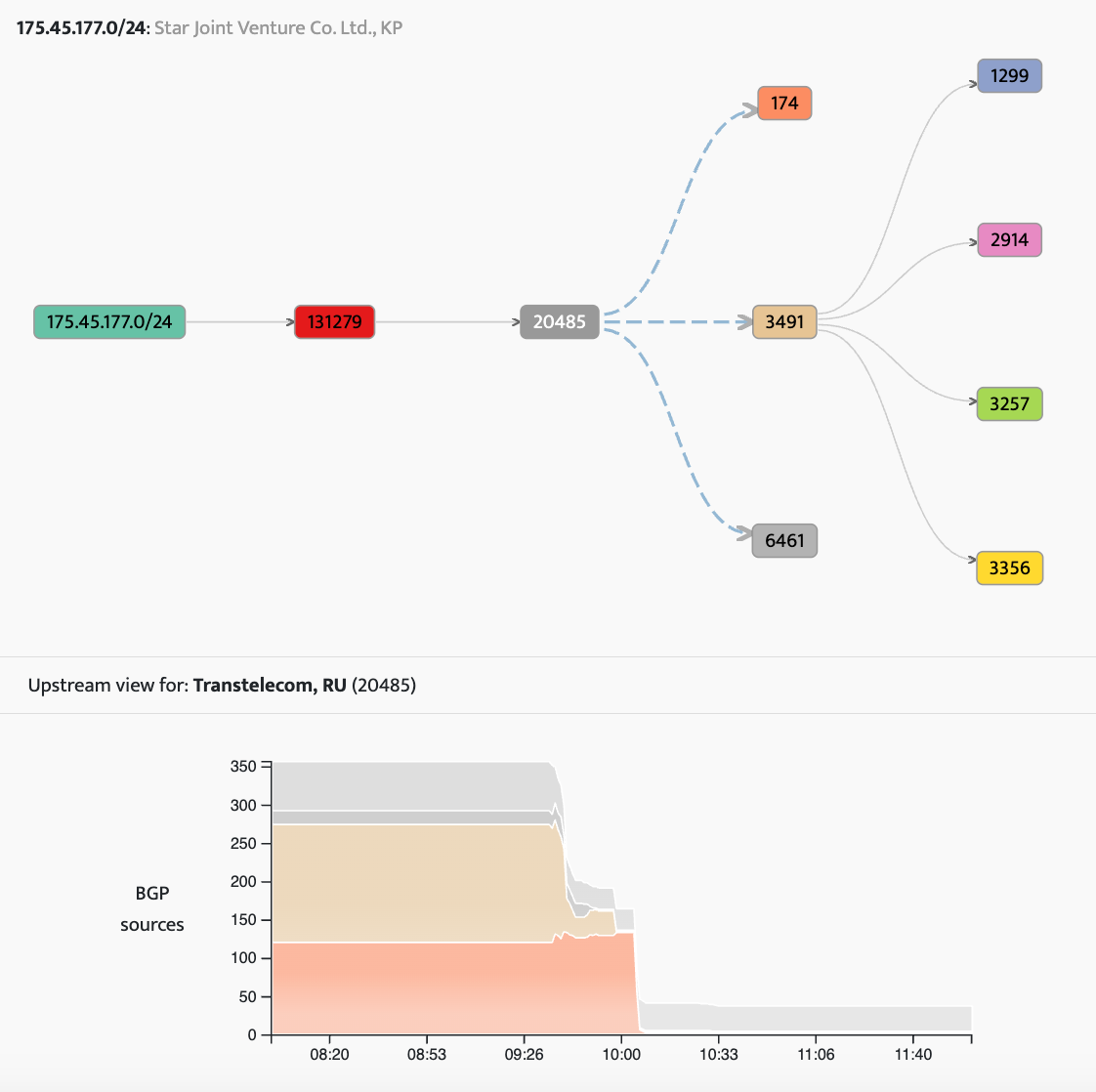
In these diagrams, the light grey represents “other” or adjacencies too weakly supported to warrant their own series. These are typically the settlement-free peers of the network which are only visible to very few BGP sources.
A mistake or intentional?
Last year, we saw the first case of RPKI ROV deliberately used a vector for DDoS when a bad actor gained access to the RIPE NCC account of Orange España and began publishing intentionally incorrect ROAs. Just like what happened in North Korea, the problematic ROAs rendered the legitimate routes RPKI-invalid, decreasing their propagation and causing an outage for Spain’s second-largest mobile operator.

But did a bad actor intentionally publish a ROA with a maxLength attribute that doesn’t match how AS131279 announces its routes?
At any given time, there are hundreds of RPKI-invalid routes being announced on the internet. Nearly all of these are invalid due to a misconfiguration in the ROA and don’t propagate very far. We’ve used these persistently RPKI-invalid routes in the past to measure the impacts of an evaluation of RPKI-invalid on route propagation.
The most common type of ROA misconfiguration that I encounter is a maximum prefix length that is shorter than the prefix lengths of the routes originated. I assume that the information in the ROA was correct at some time in the past, and then the routing changed, or there may be a fundamental misunderstanding of what the field represents.
An effective BGP configuration is pivotal to controlling your organization’s destiny on the internet. Learn the basics and evolution of BGP.

The good news for North Korea (and everyone else with a misconfigured ROA), is that a simple fix resolves this issue. Either the maximum prefix length setting can either be increased to match the prefix length of the route, or it can simply be removed causing RPKI to only match on the AS origin in the ROA. This latter course of action was published as a best practice in 2022, as maximum prefix length is an optional field.
As I was drafting the blog post, the situation resolved itself. More than 16 hours after impairing its ability to reach the global internet, North Korea published additional ROAs, causing their four routes to become RPKI-valid for the first time in history. The country’s 100% ROA coverage is admirable and hopefully can serve as motivation for their neighbor to the south, which presently stands at a paltry 0.21% coverage for IPv4, one of the lowest in Asia.
Welcome back, North Korea!