Kentik Blog
























Despite the siren song of AI in the keynotes, visitors were far more focused on solving real-world problems. These are the issues that have plagued IT practitioners for years, if not decades: troubleshooting and validating performance and availability of their applications, services, and infrastructure.
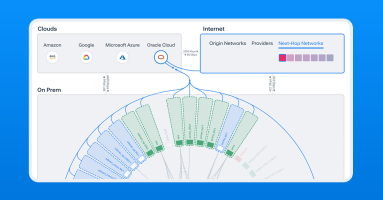
Kentik now provides network insight into Oracle Cloud Infrastructure (OCI) workloads, allowing customers to map, query, and visualize OCI, hybrid, and multi-cloud traffic and performance.
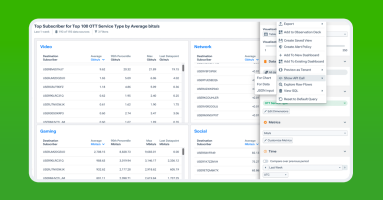
Learn how to analyze subscriber behavior using Kentik. In this post, we focus on the challenges and solutions of identifying and tracking the customers in an IP network while complying with regulations such as GDPR, show how Kentik Custom Dimensions and Data Explorer provide the analysis, and finally touch on how the associated APIs help automate and ease the entire process.
Have you ever sat down and thought to yourself, “What’s new at Kentik?” Well, you’re in luck! Welcome to the first edition of a blog series to highlight the best and brightest of Kentik that month.
Is there a gap between the potential of network automation and widespread industry implementation? Phil Gervasi explores how the adoption challenges of network automation are multifaceted and aren’t all technical in nature.
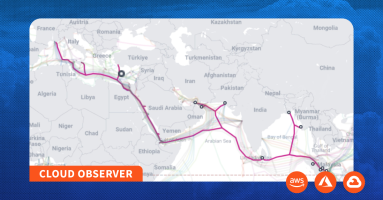
In this edition of the Cloud Observer, we dig into the impacts of recent submarine cable maintenance on intercontinental cloud connectivity and call for the greater transparency from the submarine cable industry about incidents which cause critical cables to be taken out of service.
Kubecon 2023 was more than just another conference to check off my list. It marked my first chance to work in the booth with my incredible Kentik colleagues. It let me dive deep into the code, community, and culture of Kubernetes. It was a moment when members of an underrepresented group met face-to-face and experienced an event previously not an option.
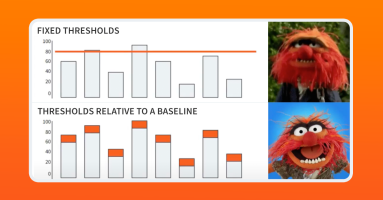
The entire reason we have monitoring is to understand what users are experiencing with an application. Full stop. If the user experience is impacted, sound the alarm and get people out of bed if necessary. All the other telemetry can be used to understand the details of the impact. But lower-level data points no longer have to be the trigger point for alerts.
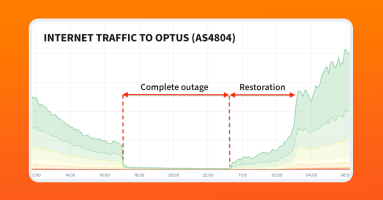
Last week a major internet outage took out one of Australia’s biggest telecoms. In a statement out yesterday, Optus blames the hours-long outage, which left millions of Aussies without telephone and internet, on a route leak from a sibling company. In this post, we discuss the outage and how it compares to the historic outage suffered by Canadian telecom Rogers in July 2022.
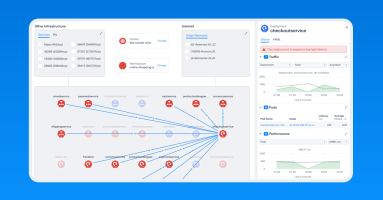
Kentik Kube provides network insight into Kubernetes workloads, revealing K8s traffic routes through an organization’s data centers, clouds, and the internet.