Kentik Blog
























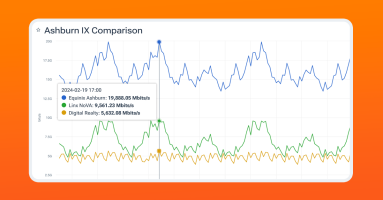
Kentik users can now correlate their traffic data with internet exchanges (IXes) and data centers worldwide, even ones they are not a member of – giving them instant answers for better informed peering decisions and interconnection strategies that reduce costs and improve performance.
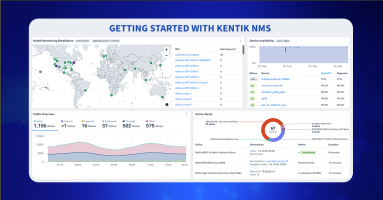
Kentik NMS is here to provide better network performance monitoring and observability. Read how to get started, from installation and configuration to a brief tour of what you can expect from Kentik’s new network monitoring solution.
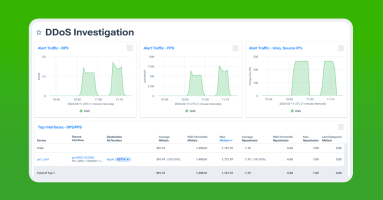
DDoS attacks disrupt services and damage reputations, with motivations ranging from political to personal. These attacks can also mask more severe security breaches, so early detection and mitigation are crucial. Learn how Kentik provides a solution by analyzing enriched NetFlow data to identify and mitigate DDoS threats.
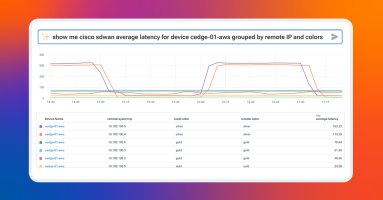
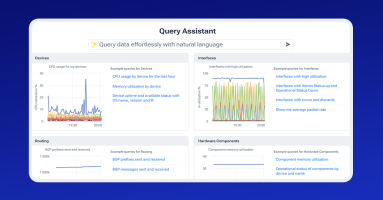
Kentik Journeys uses an AI-based, large language model to explore data from your network and troubleshoot problems in real time. Using natural language queries, Kentik Journeys is a huge step forward in leveraging AI to democratize data and make it simple for any engineer at any level to analyze network telemetry at scale.
Kentik NMS has launched and is setting sail in familiar waters. Monitoring with SNMP and streaming telemetry is only the first leg of the journey. In short order, we’ll unfurl additional options, increasing NMS’s velocity and maneuverability.
We’re bringing AI to network monitoring and observability. And adding new products to Kentik, including a modern NMS, to simplify troubleshooting complex networks.
In the rapidly evolving telecom sector, the concept of “cloudification” is not just a trend but a transformative shift, reshaping how services are delivered and managed. This change is underpinned by modern software architectures featuring modularity, microservices, and cloud-native designs. As we embrace this new era, marked by the rise of “netcos” and “servcos,” we must also navigate the complexities it brings.
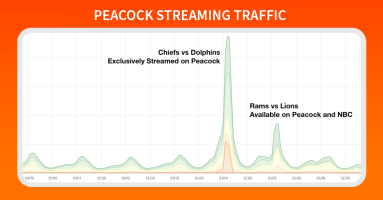
NFL playoffs are here, and Doug Madory tells us how Saturday’s first-ever exclusively live-streamed NFL playoff game was delivered without making any references to pop superstar Taylor Swift or her sizzling romance with nine-time Pro Bowler Travis Kelce.
Is SNMP on life support, or is it as relevant today as ever? The answer is more complicated than a simple yes or no. SNMP is reliable, customizable, and very widely supported. However, SNMP has some serious limitations, especially for modern network monitoring — limitations that streaming telemetry solves. In this post, learn about the advantages and drawbacks of SNMP and streaming telemetry and why they should both be a part of a network visibility strategy.
In this post, we share the joys and benefits of having pets while working from home. We discuss the scientific benefits of having pets around, including improved mental health and job performance and offer practical tips for working with pets. From providing moral support during meetings to adding fun to our workdays, our furry companions play a vital role in our daily routines at Kentik.