Kentik Blog
























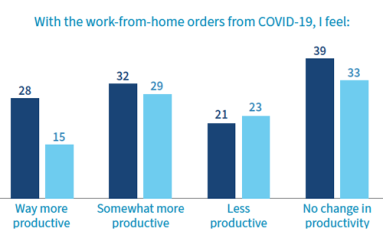
Today we published a report on “The New Normals of Network Operations in 2020.” Based on a survey of 220 networking professionals, our report aims to better understand the challenges this community faces personally and professionally as more companies and individuals taking their worlds almost entirely online.
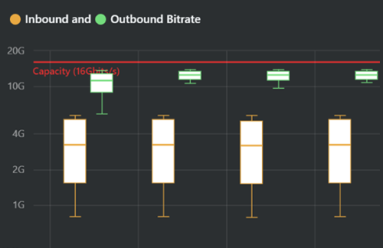
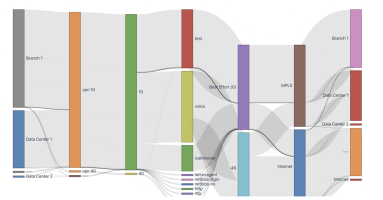
Network capacity planning traditionally required a user to collect data from several tools, export all of the data, and then analyze it in a spreadsheet or database. In this post, we highlight Kentik’s latest platform capabilities to help understand, manage and automate capacity planning.
The NFL Draft created a network traffic spike and set an example for other sports leagues considering entirely-online drafts. In this post, we show Kentik’s view of network traffic from the draft and compare it to traffic seen from the Super Bowl. We also discuss why the data shows network capacity is critical for new normals.
If you missed Akamai, Uber and Verizon Media talking about networking during COVID-19, read our recap of Kentik’s recent virtual panel. In this post, we share details from the conversation, including observed spikes in traffic growth, network capacity challenges, BC/DR plans, the internet infrastructure supply chain, and more.
SD-WAN promises to boost agility, security, performance, and management and operations. However, without effective network visibility, the path to a successful deployment is difficult to achieve. In this post, we provide considerations for solving SD-WAN visibility challenges.
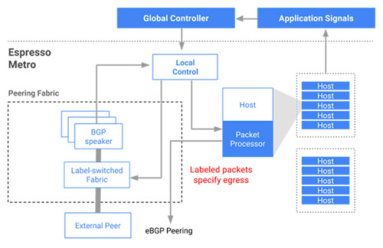
Google is investing and innovating in SD-WAN. In this post, Kentik CTO Jonah Kowall highlights what Google has been up to and how Google’s SD-WAN work can apply to the typical organization.
Kentik recently hosted a virtual panel with network leaders from Dropbox, Equinix, Netflix and Zoom and discussed how they are scaling to accommodate the unprecedented growth in network traffic during COVID-19. In this post, we highlight takeaways from the event.
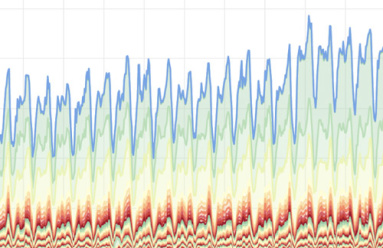
At Kentik, we’re always interested in monitoring trends in network traffic. This helps to inform our community and customers globally about potential opportunities and threats to network operations. In this ongoing blog post, we’ll provide updates to trends in traffic in correlation with COVID-19.
When more of the workforce shifts to working remotely, it puts new and different strains on the infrastructure across different parts of the network. In this post, we discuss strategies for managing surges in network traffic coming from remote employees and share information on how Kentik can help.