The State of DDoS Attacks and Defense
Summary
DDoS attacks constitute a very significant and growing portion of the overall cybersecurity threat. In this post we recap highlights of a recent Webinar jointly presented by Kentik’s VP of Product Marketing, Alex Henthorn-Iwane, and Forrester Senior Analyst Joseph Blankenship. The Webinar focused on three areas: attack trends, the state of defense techniques, and key recommendations that organizations can implement to improve their protective posture.
Recap: Webinar With Forrester Senior Analyst Joseph Blankenship
I recently had the pleasure of presenting a webinar on Distributed Denial of Service (DDoS) attacks in collaboration with Forrester Senior Analyst Joseph Blankenship. Our specific focus was in three areas: attack trends, the state of defense techniques, and key recommendations that organizations can implement to improve their protective posture. This post is a recap of some of the material we covered.
DDoS Concerns for Business
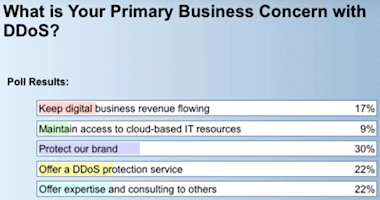
Before we kicked off our formal presentations, we thought it would be interesting to poll audience members to identify their primary business concerns related to DDoS. The audience was diverse in terms of representing organizations from across the spectrum, including service providers, digital businesses, and traditional IT organizations. As shown at left, DDoS raises a range of concerns, with the foremost being protection of the organization’s brand.
Key DDoS trends
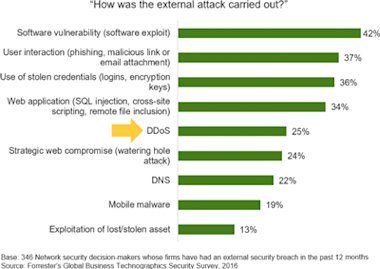
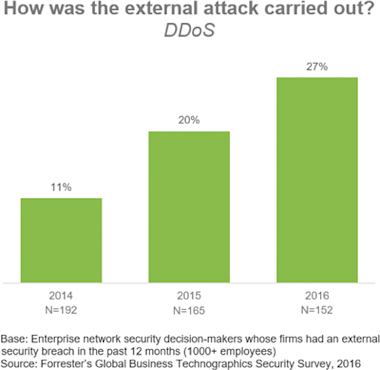
Joseph began the presentation by covering DDoS trends from Forrester’s perspective. A key observation — which shouldn’t come as a surprise but is important to keep in mind — is that DDoS attacks constitute a very significant portion of the overall cybersecurity threat. 30 percent of respondents to Forrester’s 2016 Global Business Technographics Security Survey reported suffering a cybersecurity breach as a result of an external attack, and 25% of those attacks were DDoS. Further, according to the same study, the portion of attacks that are DDoS is steadily and aggressively on the rise, as illustrated in the next graph.
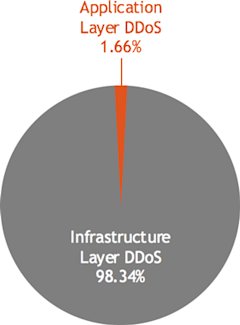
At this point Joseph handed off to me and I covered some more-technical aspects of DDoS trends. One key point, as revealed in Akamai’s Q3 2016 State of the Internet Security Report, is that the vast majority of DDoS attacks — over 98% — are focused on disrupting access to network or server infrastructure rather than on targeting application limitations or vulnerabilities. The precise mix of infrastructure attack types changes over time depending on how attackers think they can get the most leverage from their efforts. But while the proportion may vary, the presence of a few usual suspects is constant. The Akamai report identifies these top infrastructure attack vectors as UDP fragmentation, Domain Name Service (DNS) reflection, and Network Time Protocol (NTP) reflection.
Another interesting fact is that while last year’s mega-attacks against OVH, Brian Krebs, and Dyn got most of the media attention, there is, according to the Neustar Fall 2016 DDoS report, a sweet spot for the traffic volume involved in DDoS attacks, which is in the range of 500 Mbps to just under 10Gbps.
IoT as a Cyberweapon
Next up was a look by Joseph at how IoT devices have been turned against us, contributing to the DDoS problem. He covered IoT attack surfaces, how IoT contributed to the mega-attacks mentioned above, the timeline of the Mirai botnet, and the IoT concerns of cybersecurity leaders within IT organizations. Interestingly, DDoS ranked as the second-highest IoT cybersecurity concern in both the previously mentioned 2016 Forrester security report and its 2015 predecessor.
The State of DDoS Protection
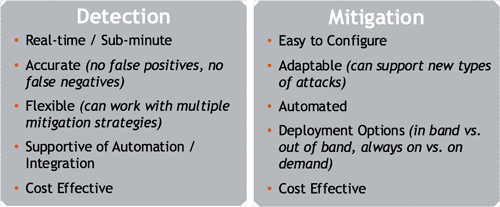
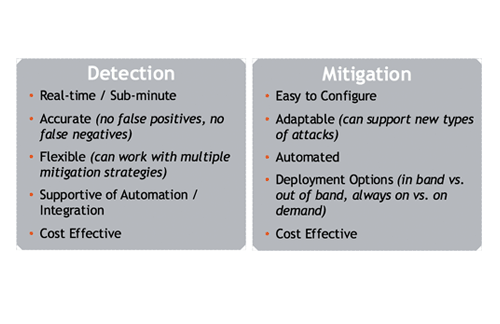
In our next section we covered some issues around how DDoS protection is handled, beginning with a look at the main requirements for modern DDoS defense. While these may seem like no-brainer points, it’s interesting to note that according to the Neustar report, only 30% of DDoS attacks globally are detected in under an hour. A major reason for this is that a tremendous amount of DDoS detection as practiced in the industry today involves manual intervention.
To speed detection and response, detection must be accurate enough to allow for fully automated mitigation. But there’s a major limitation to achieving that level of accuracy, which is the continued use of single-server appliances for DDoS protection. In the webinar, I laid out how constrained these appliances are in terms of both computation and storage. These limits cause suboptimal detection due to:
- Monitoring ranges of IP addresses rather than individual IPs.
- Incomplete baselining: - Per router/flow exporter (not network-wide); - Single dimension monitoring & alerting.
- Static policies that quickly fall out of sync with reality.
The above factors lead to significant false negatives. On top of that, appliance-based DDoS detection approaches offer nearly zero analytics for forensics and situation-awareness, and they have very limited, almost non-functional APIs.
Naturally I took the opportunity to contrast these appliances with Kentik’s DDoS protection solution. Kentik Detect offers the industry’s most accurate detection because:
- It can track millions of individual host IPs.
- It performs far more sophisticated baselining and anomaly detection on network-wide data.
- It performs multi-dimensional monitoring.
- It includes sophisticated multi-threshold alerting policies with auto-adaptive baselining and auto-triggered mitigation (built-in or via third-party integration).
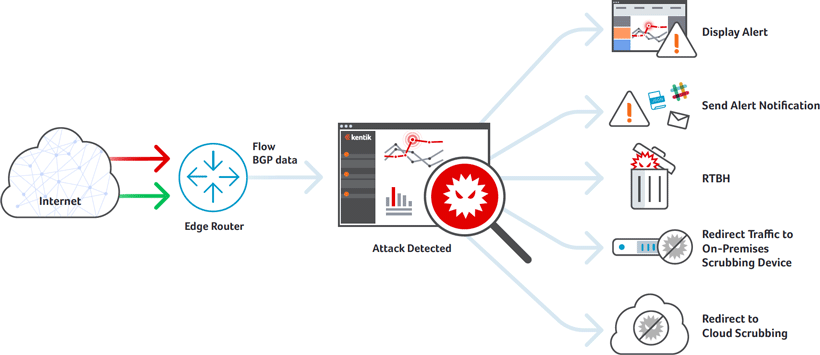
On top of far greater detection accuracy, Kentik Detect offers big data network analytics for deep visibility and awareness.
Recommendations
Building on what we’d covered so far, Joseph offered three major recommendations for protection:
- Implement a two phase mitigation strategy with both downstream and upstream mitigation.
- Ensure that DDoS attacks are incorporated into incident response plans.
- Take into account other sources of service disruption, such as DNS service provider outages.
From the Kentik perspective, I recommended that the audience consider a true hybrid approach to detection and mitigation. The world has moved far beyond the days when DDoS protection meant a single-vendor stack of devices. It’s possible to use a best-of-breed SaaS detection and analytics solution like Kentik Detect, paired with hybrid mitigation from on-premises appliances, cloud providers, and routing-based black-holing.
One example of this hybrid approach is now deployed at regional ISP PenTeleData, which had been struggling with a legacy, single-vendor system that was missing a lot of attacks and causing a significant amount of pain to their network operations team. PenTeleData replaced that system with a solution pairing Kentik Detect (for detection and analytics) with Radware hybrid mitigation, including both on-premises and cloud-bursting components. The results were dramatic: PenTeleData experienced a 30% improvement in catching and stopping DDoS attacks.
Watch it. Learn More. Try it.
All in all it was great fun collaborating with Joseph on the webinar. We covered several other topics that we don’t have space to recap here, including statistics on where most DDoS attacks originate geographically as well as the number of repeat attacks on businesses. Check out the full webinar to get more details and see the results of our second audience poll, in which we asked: “How tangible is the DDoS threat to your business?” If you’d like to learn more about Kentik Detect, you can request a demo. Better yet, experience for yourself the power of big data DDoS protection and analytics by signing up today for a free trial.



