DDoS Detection
Overview of DDoS Detection
DDoS detection is the process of distinguishing distributed denial of service (DDoS) attacks from normal network traffic in order to perform effective attack mitigation. The primary goal of a DDoS attack is to either limit access to an application or network service, thereby denying legitimate users access to the services.
There are many types of DDoS attack schemes that are used today and they are steadily becoming more sophisticated. However, their common goal is to overwhelm targeted network resources with traffic or requests for service from many different sources — potentially hundreds of thousands or more. This effectively makes it impossible to stop the attack simply by identifying and blocking a single IP address. The sheer distribution of attacking sources also makes it very difficult to distinguish legitimate user traffic from attack traffic when spread across so many points of origin.
The first step in avoiding or stopping a DDoS attack is knowing that an attack is taking place. To detect an attack, one has to gather a sufficient network traffic information, then perform analysis to figure out if the traffic is friend of foe. This process can be performed manually or in an automated fashion. DDoS detection is the key to quickly stopping or mitigating attacks and in order for this to happen, two success criteria need to be met:
- Speed of detection
- Accuracy of detection
So detection methods are a key consideration in formulating a strong DDoS defense.
The DDoS Threat
There is no doubt, as evidenced in the alarming rise of DDoS attacks, that DDoS detection is an absolute necessity for businesses that rely on internet traffic in order for them to avoid disruption of applications and services, revenue loss, and brand damage. As of late 2025, DDoS activity remains elevated, powered in part by new technologies including agentic AI and large language models (LLMs), which have lowered the barrier to entry for would-be attackers and enabled “hypervolumetric” attacks.
A variety of technology vendors and government organizations regulary publish reports on DDoS attack and DDoS protection trends and their findings highlight that DDoS attack volume remains consistently high and that these attacks cause real damage to organizations. Some highlights from 2024-2025:
- Cloudflare blocked 20.5M attacks in Q1 2025.
- NETSCOUT recorded 8M+ attacks in 1H 2025.
- A report from Help Net Security found that an average DDoS attack now lasts 45 minutes—an 18% increase from 2023—costing unprotected organizations approximately $270,000 per attack at an average rate of $6,000 per minute (roughly $360,000 per hour). It’s clear that mean-time-to-remediation is crucial for organizations confronted with DDoS attacks.
- CISA’s Zero Trust microsegmentation guidance (July 29, 2025) suggests that continuous network visibility and segmentation controls are essential components of protecting against DDoS attacks and other network security threats.
Additional negative business consequences related to DDoS attacks include:
- Increased risk of SLA violations and customer churn
- Escalating operational costs from manual attack triage
- Transit overprovisioning and egress waste, as much as 10–30%
While the costs associated with DDoS attacks have increased over time, the risks are not new. [A Neustar, Inc. report] from 2016 (https://www.neustar.biz/2016-fall-ddos-report “Neustar report on DDoS Attacks”) from 2016 found that DDoS attack volume was both persistent and widespread. Some highlights from that report:
- DDoS attacks are unrelenting and show no sign of abating: The overwhelming majority of surveyed organizations (73 percent) suffered a DDoS attack. Eighty-five percent of attacked organizations were attacked more than once and 44 percent were attacked more than five times.
- DDoS attacks are only the tip of the spear in complex assaults: The majority of organizations that suffered a DDoS attack (53 percent) also experienced some form of additional compromise. Forty-six percent of breached organizations discovered a virus, malware was activated at 37 percent of breached organizations, and ransomware was encountered at 15 percent of breached organizations.
- DDoS attacks are time-consuming and expensive: It can take hours to detect and mitigate a DDoS attack at significant cost to the organization. Seventy-one percent of organizations took an hour or more to detect a DDoS attack and 72 percent took an additional hour or more to respond to the attack. Forty-nine percent of surveyed organizations lose $100,000 or more per hour of downtime during these attacks.
Learn how to protect your network before an attack causes damage to your customers or reputation.

In-line versus Out-of-band DDoS Detection
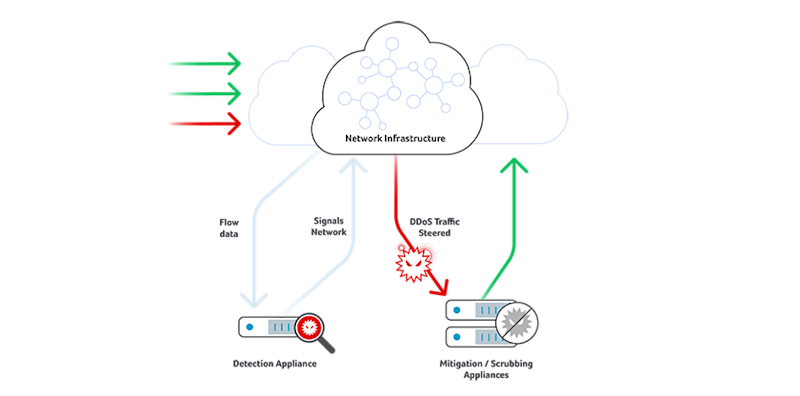
There are two primary means of detecting DDoS attacks: in-line examination of all packets and out-of-band detection via traffic flow record analysis. Either approach can be deployed on-premises or via cloud services. The basic in-line DDoS detection capabilities of network devices such as load balancers, firewalls or intrusion prevention systems may have once provided acceptable detection when DDoS attacks were smaller but high-volume attacks can overwhelm these devices, since they utilize memory-intensive stateful examination methods.
Dedicated DDoS mitigation appliances are the primary way to accomplish in-line detection (and remediation) today. However, they can become costly and have a short life cycle in the face of higher volume threats. These appliances are still necessary and relevant for mitigation because ASIC and network processor power is needed for deep packet inspection when scrubbing traffic but for cost-effectiveness and scaling reasons, moving detection out of mitigation devices has become the norm.
Out-of-band DDoS detection is accomplished by a process that receives flow data from NetFlow, J-Flow, sFlow, and IPFIX-enabled routers and switches, then analyzes that flow data to detect attacks. Mitigation of the attacks is then triggered manually or automatically, via routing or appliance-based methods.
DDoS Detection: Improving Accuracy Using Big Data
The first generation of out-of-band DDoS detection solutions were based on single server software design, mostly running on standalone rack-mounted server appliances.
While far better than nothing, single servers simply don’t have the compute, memory and storage resources to track high volumes of traffic data on a network-wide basis. This is particularly true when attempting to perform dynamic baselining, which requires scanning massive amount of flow data to understand what is normal, then looking back days or weeks in order to assess whether current conditions constitute an anomaly. Regardless of whether it is deployed on-premises or in the cloud, single server DDoS detection is insufficient to accurately detect today’s attacks in a consistently reliable fashion.
By leveraging big data technologies for storing network events as they happen and by accessing this data repository in the cloud, customers can avoid DDoS detection appliances that fail to scale as their on-premise networks grow and/or re-deploy in the cloud, or avoid expensive in-house projects that require ongoing investments or obsolete as open software frameworks change.
About Kentik DDoS Detection & Related DDoS Protection Resources
Kentik Protect offers the industry’s only big-data network visibility and DDoS defense solution built from the ground up on big data and delivered as a cost-effective SaaS. Kentik offers the industry’s most accurate DDoS detection, and can automatically trigger mitigation via RTBH, Cloudflare, Radware DefensePro or A10 Thunder TPS mitigation.
For more information on how network observability can provide superior DDoS detection speed and accuracy, check out the blog post “8 reasons why network observability is critical for DDoS detection and mitigation”, watch the Superloop video, and read our guide, “The NetOps guide to network security”.
Find all of our latest resources about DDoS attacks, BGP hijacking, and other network security threats on our DDoS Protection and Network Security Package page.
Know you want to get started with superior cloud-based DDoS detection and mitigation today? Start a free trial of Kentik or request a demo of our DDos solution.
FAQs about DDoS Detection
How can I detect and prevent volumetric DDoS without false positives?
Kentik leverages big-data flow telemetry, BGP, and interface metrics — combined with machine-learning-driven traffic profiling — to distinguish attack traffic from legitimate traffic, reducing false positives. When volumetric DDoS is detected, Kentik Protect can trigger automated mitigation (via RTBH, FlowSpec, upstream scrubbing), helping prevent or mitigate the attack before it impacts users.
Why is DDoS detection difficult?
DDoS attacks are distributed across many sources (potentially hundreds of thousands), which makes it hard to block “one bad IP” and hard to separate legitimate traffic from attack traffic when origins are so widespread.
What are the two most important goals of DDoS detection?
Fast and accurate detection are the two success criteria: you need to identify attacks quickly while minimizing misclassification of legitimate traffic.
What’s the difference between in-line and out-of-band DDoS detection?
In-line detection inspects packets directly on devices like firewalls or IPS, while out-of-band detection analyzes traffic using flow records. Both approaches can run on-prem or as cloud services.
Why do high-volume DDoS attacks overwhelm in-line detection tools?
Basic in-line capabilities rely on memory-intensive, stateful examination methods that can be overwhelmed by modern high-volume attacks.
What telemetry is typically used for out-of-band DDoS detection?
Out-of-band detection commonly ingests flow data from NetFlow, J-Flow, sFlow, and IPFIX-enabled routers and switches, then analyzes those records to detect attacks.
How does out-of-band detection trigger DDoS mitigation?
Once an attack is detected from flow analysis, mitigation can be triggered manually or automatically using routing-based or appliance-based methods.
Why do modern DDoS detection systems need big-data architecture?
Accurate detection often requires dynamic baselining over large volumes of traffic and looking back days or weeks for comparison. Single-server detection lacks the compute, memory, and storage to do that reliably at network scale.
Why do NetOps teams separate DDoS detection from mitigation appliances?
Mitigation appliances remain useful for deep packet inspection and scrubbing, but for cost and scaling reasons, detection often moves out of those devices and into out-of-band analytics solutions like Kentik.