How to Evaluate Network Monitoring Tools
Technologies and paradigms, such as edge computing and multicloud networking, have revolutionized how networks process and transfer data. However, they’ve also increased the complexity of network monitoring and management. As IT infrastructures become increasingly heterogeneous, network administrators and engineers require more sophisticated tools to gain complete visibility into their networks. Given the abundance of network monitoring solutions available, deciding which one deserves your time and money can be challenging.
With the proliferation of the Internet of Things (IoT), cloud adoption, and high-bandwidth applications, it’s imperative that your network monitoring solution enables you to keep track of all the disparate IT assets within your infrastructure. It seems simple enough in concept. However, the way network monitoring tools allow you to gain and maintain visibility isn’t always a cut-and-dried process.
This guide provides a deep dive into assessing network monitoring tools. By the end of it, you should be able to distinguish a good monitoring solution from a mediocre one—at least for your use case.
Types of Network Monitoring
At its most basic level, network monitoring revolves around surveilling how data travels through your IT infrastructure. You need a way to gain observability of the relationships between its mechanisms and processes, and there are several ways that network monitoring tools allow you to achieve this.
Network Traffic Monitoring: Flow Analysis
As data passes through the various devices and interfaces in your network, your network hardware captures information about the data, such as source and destination ports, protocol details, timestamps, and IP addresses. This information can be exported and analyzed, allowing you to glean the nature of the data flowing through your network and the devices it interacts with.
The most effective way to perform this analysis is by using data flow sampling technologies, such as NetFlow and its variations (such as jFlow and sFlow). Most sampling technologies function through an agent (exporter) that collects traffic information and uses it to generate flow records as it enters or exits a network device interface. It then exports the flow records to a collector, a piece of software that usually runs and stores information on a database server.
Analysis software then gathers this data, interprets it, and displays it in a consumable way. It allows you to profile your network traffic and identify the various protocols and mechanisms that drive it to detect any anomalies or suspicious activities:

From a big-picture perspective, you can use the information captured from network flow analyses to optimize your network’s performance, improve overall resource utilization, reduce network administration costs, and increase efficiency in capacity planning and scaling. It also makes troubleshooting easier and allows you to detect potential breaches and security threats, which in turn ensures that your business is compliant with the latest industry regulatory standards.
Network Device Monitoring: SNMP and Streaming Telemetry
Currently, Simple Network Management Protocol (SNMP) and streaming telemetry (ST) are two of the most accepted ways of collecting network device metadata and metrics.
How SNMP Works
SNMP functions through a dedicated collection of agents and managers, which you can give specific tasks to perform. These entities typically come in the form of software services or applications running dedicatedly on separate network devices.
For instance, an SNMP agent usually runs on a router, gateway, or switch. Its main function is to collect information about the device’s operation and performance. This data is stored in a database known as a management information base (MIB).
SNMP managers most commonly run on servers. Their main functionality is to initiate requests from SNMP agents. Although the data extraction frequency depends on each case or need, SNMP focuses more on real-time network monitoring. Thus, SNMP managers are usually set to request information from their designated agents in minute- or hour-long intervals.
An SNMP configuration that collects data regarding your network data consumption looks something like this:

In the preceding configuration, the SNMP agent is a router that passes MIB files through its network configuration using object identifiers (OIDs) that allow it to find all network devices. Network administrators use an SNMP manager to extract data from the SNMP agent in specific intervals (for example, every hour). They use this data to analyze the network’s data consumption tendencies, compare them to past results, and take appropriate action if required.
SNMP is especially suitable for IT infrastructure that features a large collection of devices that need to be continuously monitored. Most major network hardware device vendors, such as Broadcom, D-Link, and Cisco, have built SNMP support into their devices, which gives network engineers a uniform way to gather information from these devices, regardless of vendor. SNMP is also open source, which makes it easy for network engineers to adopt and means it can be customized according to the needs of users or organizations.
SNMP is still one of the most widely used network monitoring protocols, chiefly because of its simplicity. However, its lack of sophistication can increase demand and overhead and can result in limited data granularity. For instance, the example earlier essentially circulates files or packets (datagrams) around the network with very little discretion into how it functions. So, while it gives you real-time data, it also adds strain to the network.
How Streaming Telemetry Works
Streaming telemetry is a more precise alternative to SNMP, where network devices actively send data to you in real-time. Streaming can be continuous, set to occur in intervals (cadence-based telemetry), or triggered by an event (event-based telemetry).
Streaming telemetry uses a push model as opposed to SNMP’s polling. Network devices are set to automatically transmit data to a collector without a trigger from an agent, as is the case with SNMP. The differences don’t just stop there. SNMP chiefly relies and functions on the User Datagram Protocol (UDP)—a connectionless protocol that can be oftentimes unreliable. In addition to UDP, streaming telemetry can be configured to use the Transmission Control Protocol (TCP) or remote procedure call (gRPC, XML-RPC).
Streaming telemetry supports data models such as OpenConfig and the YANG Catalog. Businesses and engineers can also use their own proprietary models if they have the means and desire to do so. All these implementation options make streaming telemetry a more flexible solution than SNMP. Streaming telemetry also offers greater granular control and is far more scalable.

Streaming telemetry allows you to reliably collect high-resolution performance data in real time. However, there can be a downside to this, especially if you’re running a suboptimal implementation that uses TCP. Streaming telemetry through TCP can be heavy on memory and network resources as connections must be established before data can be transmitted or exchanged. UDP is a more lightweight solution.
Is it time to migrate to a modern network monitoring system?

Network Traffic Simulation: Synthetic Transaction Monitoring
The previously mentioned techniques are mostly reactive, but your network monitoring tool’s features should also allow you to proactively measure your network’s performance, especially if large volumes of data regularly pass through your network.
Synthetic transaction monitoring (STM) allows you to test or simulate how your network will behave or react under a set of predefined scenarios. It functions similarly to mocking or browser automation for software testing. A typical approach uses scripts that replicate the actions users and/or clients may perform while interacting with the network to mimic network traffic. The results of these sessions can give you crucial insights into how well your network will perform under strain or heavy traffic to proactively identify bottlenecks and other issues that may negatively impact the quality of service (QoS) even before your network is live.
A synthetic transaction monitoring tool can also let you keep tabs on application and device uptime to identify entities or products with suboptimal resource utilization. You can also set your synthetic transaction monitoring tool to focus on specific business transactions, alerting you to any issues that may occur in real time. This makes it a particularly useful tool for organizations and companies specializing in web service and application development. For example, you can use it to determine how quickly your servers respond to or process API calls sent from client machines.
Key Features to Consider When Evaluating Network Monitoring Tools
So why do the earlier networking monitoring techniques matter, and how do they relate to network monitoring tools? One of the first things to consider when evaluating a network monitoring tool is the range of techniques it supports, which determines its monitoring capabilities.
Monitoring Capabilities
A good network monitoring tool should support most (if not all) of the techniques covered in the previous section. While these methods can sometimes be misunderstood as competing products, that isn’t the case. It’s usually most efficient to employ different ones for specific use cases.
For example, you can use streaming telemetry and data flow analysis to detect network security threats, receive alerts for downed devices, measure performance, and process other urgent information. However, you can use SNMP to deliver less time-sensitive information, such as the baseline health of network products or the number of client machines (virtual and otherwise) currently running and connected to the network. You can also use SNMP to manage your configurations and monitor automation and deployments (in the case of continuous integration, continuous delivery (CI/CD) pipelines). Synthetic transaction monitoring can be used to test out new network configurations or additions.
Your network monitoring tool should provide a well-organized dashboard that helps you organize or (in some cases) unify the information gathered from all these different endpoints.

Keep in mind that while you may not necessarily require all these capabilities for your current network setup, you might need them in the future. Hence, it’s best to select a scalable solution with sufficient customizability.
Data Collection and Aggregation
In addition to being able to source data from a litany of channels and techniques, your solution should be able to organize this information in a meaningful and easily comprehensible way. While it’s essential that it continuously observes the network and notifies you of any performance hiccups in real-time, it should also allow you to compare your network against market baselines. For example, you can measure how well your network handles file transfers against networks structured similarly to yours.
Solutions that offer border gateway protocol (BGP) or other peering data aggregation and network connection features can be used to improve your network’s (internet) performance and ensure the network-based services you deliver are as optimal as can be.
Alerting and Notification
In addition to a well-structured user interface, your network monitoring tool should alert you of any significant events, enabling you to respond promptly to issues that require decisive action. As your network scales and becomes more complex, actively tracking the traffic along with every device and node in your network becomes increasingly challenging. Notifications and alerts make surveilling your network easier.

While many network monitoring tools feature alerts and notifications, they tend to have limited customizability or lack channels and integrations through which to send notifications. For example, it’s a good idea to verify if your network monitoring tool offers a set of customizable preset thresholds or allows you to define your own collection. You may want the monitoring solution to alert you when data consumption or latency (ping time) reaches a specific, defined limit.
The tool’s notification channels should be conducive to how your business and/or tech department is set up. You probably already have an idea of who should be sent alert notifications and how. As you assess performance tools, keep the following questions in mind:
- Can your network monitoring solution facilitate this communication?
- Does it support the necessary channels?
- Does it have SMS, email, Discord, Slack, and other instant messaging integrations?
- If your organization has its own in-house chat or instant messaging channels, can the network performance tool’s alerting features be integrated with that channel?
Reporting and Analytics
Your network monitoring tool should, of course, be able to collect and store data from disparate channels. It should also allow you to transform this data and use it to gain useful, timely insights.
A solution that offers (multiple) customizable dashboards that can be launched or kept on-screen lets you quickly view contextually meaningful information. A large variety of visualization tools, such as network maps, graphs, and charts, provides you with several ways to view your network’s topology.
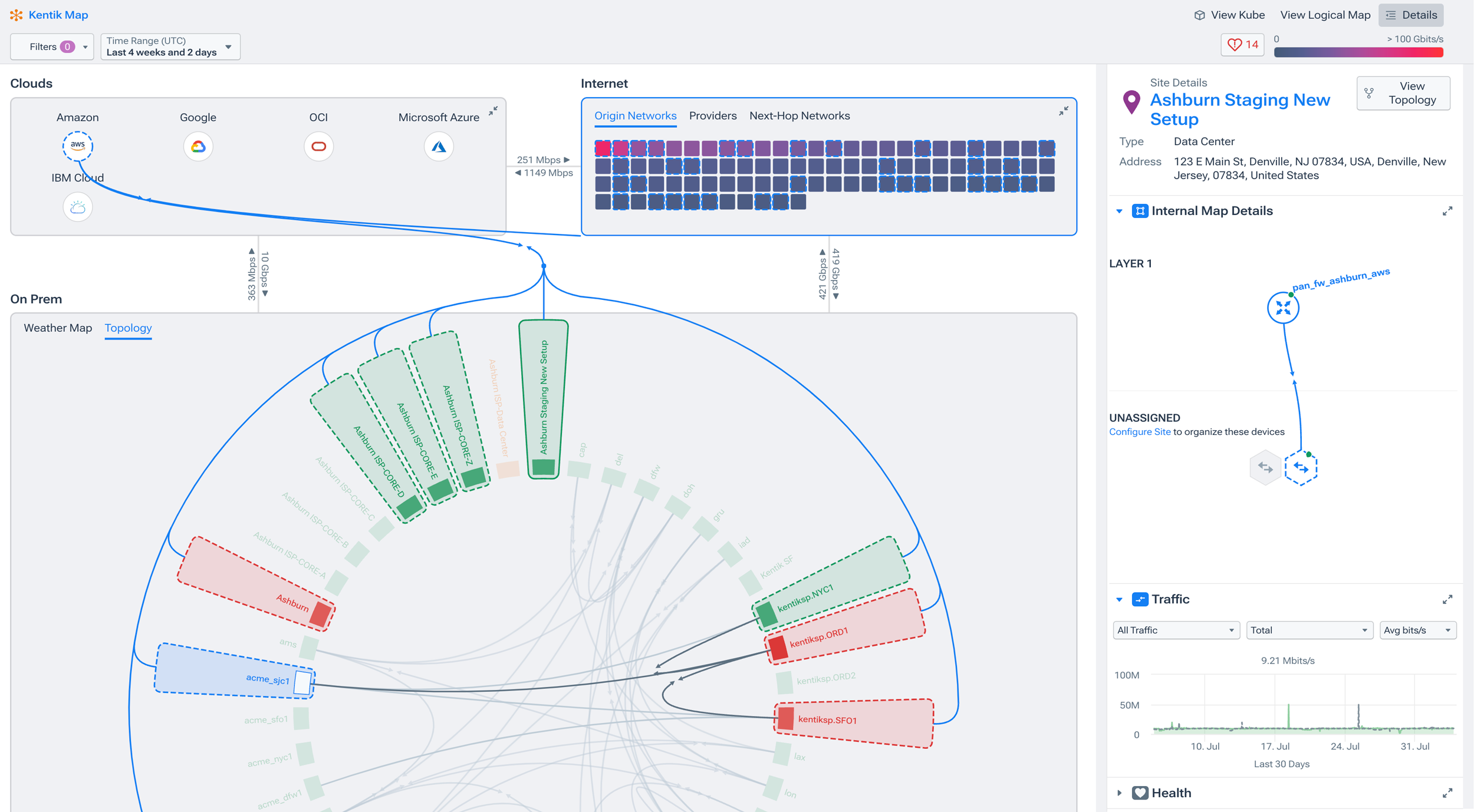
Network performance often plays a big role in business performance. If you must report on your network’s performance metrics, choose a tool that lets you produce rich, exportable reports that can be easily consumed by non-technical stakeholders, like chief operating officers (COOs) and finance managers.
A network performance tool that stores an archive of reports, logs, and other metadata-related files allows you to analyze and compare historical data to gauge the success of network optimizations or changes. It also aids in capacity planning and tracking how well newly implemented security measures are working.
Scalability and Security
Your network performance monitoring tool should support on-premise, cloud-based, and hybrid/multicloud network configurations. This is especially important for organizations planning to migrate their network infrastructures from on-premise to cloud. Picking a network monitoring tool that can scale alongside your network ensures that you won’t have to replace that tool in the future.
Scaling up your network can often scale up risks, too. The more you expand your network, the more difficult it becomes to manage. Your IT infrastructure’s attack surface expands as you add new devices and users, so it’s important that your network monitoring tool allows you to detect and mitigate cyberthreats, such as distributed denial-of-service (DDoS) attacks.
Your network monitoring tool should be able to help you detect vulnerabilities, such as non-granular access permissions and weak user authentication mechanisms on client machines, servers, and other applicable network devices. For example, it’s a good idea to enforce multifactor authentication (MFA) where appropriate. Your network monitoring solution should be able to help you identify the areas in which it would be best to add MFA and help you manage it as well. As another example, if you do decide to use the Remote Authentication Dial-In User Service (RADIUS) protocol to assist with onboarding and Wi-Fi authentication, your network monitoring tool should be able to (or at least help you) keep logs and monitor user sign-ins.
Another important feature is the solution’s ability to allow you to view and assess the various cybersecurity measures you’ve deployed, including firewalls and data encryption protocols, such as the Secure Sockets Layer (SSL), virtual private network (VPN), and Secure Shell Protocol (SSH).
Open Source vs. Commercial Network Monitoring Tools
Open source and commercial network monitoring tools each have their own strengths and are suited to different situations. Open source tools like Nagios, Zabbix, Cacti, OpenTelemetry, and OpenNMS are free and can be a great choice for small and medium-sized organizations that need a cost-effective solution. They are developed and maintained by open source communities and offer a high level of customization.
An open-source solution’s codebase is typically made public through a Git-based repository that you can clone or fork. You can operate it as is or add your own customizations and then package and run the tool from a server or client of your choice. Most commonly, open-source network monitoring tools require effort to configure and run. The source code can also be poorly maintained and plagued with security vulnerabilities. Depending on how popular or well-supported the tool is, you’ll mostly rely on community support for troubleshooting.
If you opt for an open source tool, keep in mind that you’ll need experienced in-house experts who can run and maintain it efficiently. So even if using the tool doesn’t come at a cost, finding and training the right staff, creating documentation for your implementation, and adding the necessary infrastructure to run the tool may be costly.
Commercial networking tools, in contrast, are typically more expensive but offer a more comprehensive set of features and better support. While organizations of all sizes might opt for a commercial tool, they’re especially appealing for large enterprises that require extensive network monitoring and management capabilities. They also come with a host of out-of-the-box features, such as templates, preconfigured dashboards, a large library of visualization options, integrations/plugins, and professional support that can be reached through a variety of channels.
Because they’re closed source, commercial tools tend to be far more secure than their open source counterparts. And if anything goes terribly wrong while using the tool, there is some peace of mind that you’ll be able to hold the vendor accountable.
Final Thoughts
The right network monitoring tool can significantly enhance your network’s performance, security, and reliability, making it an investment worth making. Evaluating network monitoring tools requires careful consideration of the tool’s scalability, real-time monitoring, alerting, reporting, and ease of use. You must also consider compatibility with your existing infrastructure, cost-effectiveness, and vendor support.
In the end, your decision should be based on your organization’s specific needs—now and in the future—as well as your budget and IT resources.
Learn More About Kentik’s Network Monitoring Tools
Kentik offers a suite of advanced network monitoring solutions designed for today’s complex, multicloud network environments. The Kentik Network Observability Platform empowers network pros to monitor, run and troubleshoot all of their networks, from on-premises to the cloud. Kentik’s network monitoring solution addresses all three pillars of modern network monitoring, delivering visibility into network flow, powerful synthetic testing capabilities, and Kentik NMS, the next-generation network monitoring system.
To see how Kentik can bring the benefits of network observability to your organization, request a demo or sign up for a free trial today.

