NetFlow Guide: Types of Network Flow Analysis
Network operators often face numerous challenges when it comes to analyzing network traffic and making informed decisions for optimizing performance and security. As networks grow increasingly complex, the need for a comprehensive solution to effectively manage network data has become more critical. NetFlow emerged as a powerful tool to address this need, providing valuable insights into network traffic patterns and usage. By leveraging NetFlow for network traffic analysis, operators can gain a deeper understanding of their infrastructure, enabling them to overcome common obstacles and ensure efficient and secure network operations.
What is NetFlow Analysis?
NetFlow is a protocol developed by Cisco. It is used to record metadata about IP traffic flows traversing a network device such as a router, switch, or host. A NetFlow-enabled device generates metadata at the interface level and sends this information to a flow collector, where the flow records are stored to enable network traffic analytics. A network operator can use NetFlow data to analyze traffic patterns and determine network throughput, packet loss, and traffic congestion at a specific interface level.
NetFlow Variants
While the term “NetFlow” is commonly used to refer to all types of flow records, there are actually three other important variants in regular use:
- IPFIX is an IETF standard flow record format that is very similar in approach and structure to NetFlow. (You can get a deeper dive on the differences in our Netflow Overview.)
- J-Flow from Juniper Networks, which essentially conforms to NetFlow v5.
- sFlow was introduced and promoted by InMon Corp but unlike NetFlow it relies on statistical sampling methods for documenting flows.
The term xFlow, while not a variant, is the generic term often used to refer collectively to all flow record variants⎯NetFlow, IPFIX, J-Flow, sFlow, etc. You can read more about flow protocols here.
Cisco has developed various versions of NetFlow, with v5 and v9 being the most widely used. NetFlow v9 introduced support for flexible and extensible flow record formats, making it more adaptable to different network scenarios. Understanding the differences between versions and selecting the most appropriate NetFlow version for your network environment is crucial.
How Does NetFlow Analysis Work?
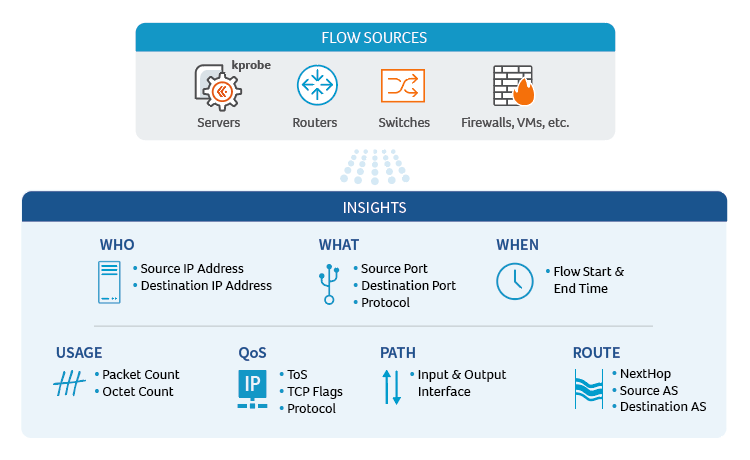
NetFlow analysis is a powerful technique that enables network operators to gain valuable insights into their network traffic patterns and usage. The process begins with the collection of metadata about IP traffic flows traversing a network device, such as a router, switch, or host. These devices, when configured with NetFlow support, generate flow records that contain essential information about the traffic, including source and destination IP addresses, port numbers, packet and byte counts, timestamps, and other relevant attributes.
As new IP traffic flows are detected, the NetFlow-enabled device creates and updates flow records in its cache. Once a flow is terminated or has been inactive for a specific duration, the device exports the flow record to a designated flow collector. This flow collector is responsible for receiving, storing, and pre-processing the flow records from multiple NetFlow-enabled devices.
The next step in the NetFlow analysis process involves an analysis application that processes the collected flow records. This application can generate reports, alerts, dashboards, and other visualizations to help network operators make informed decisions about their network’s performance, security, and resource allocation. By examining these flow records, operators can identify trends, detect anomalies, and pinpoint potential issues that may impact the network’s overall health.
The resulting insights provide network operators with the necessary information to optimize their networks performance, enhance security, and make data-driven decisions to overcome the common challenges associated with managing complex network environments.’
NetFlow Components
NetFlow monitoring solutions are typically comprised of three main components:
- Exporter: A NetFlow-enabled device generates flow records and periodically exports them to a flow collector. The Exporter identifies a flow as a unidirectional stream of packets having in common (at least) the following attributes: IP source address, IP destination address, Source port number, Destination port number, Layer 3 protocol field, and Type of Service.
- Collector: A program running on a server or cloud infrastructure that receives, stores, and pre-processes flow records from NetFlow-enabled devices.
- Application: An analysis application that processes flow records collected by the flow collector into reports, alerts, dashboards, and other results.

NetFlow Analysis for Performance Monitoring
A given set of packets is defined as a flow, which makes up the core metadata (i.e., information about the flow rather than the information that’s actually in the packets) that is included in a NetFlow “flow record.” When a new unidirectional IP traffic flow starts traversing a device, a new NetFlow flow record is created and tracked via the device’s on-board cache. Time analysis of the flow records enables performance monitoring across the network between various network elements, as NetFlow devices in total continuously export their information for processing by an analysis application.
NetFlow Analysis Use Cases
Using NetFlow offers insight to overcome many common challenges encountered by network operators including:
- Monitoring major contributors of network traffic
- Understanding application traffic and its network impact
- Optimizing internet peering relationships
- Troubleshooting and understanding network congestion points
- Detecting unauthorized WAN traffic
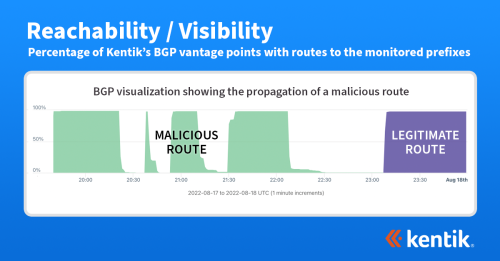
- DDoS and anomaly detection
- Validating QoS parameters
This enables various internal organizations such as network operations, engineering, planning, architecture, and security to use NetFlow analysis as a primary source of network intelligence. Consolidated NetFlow traffic analysis can reduce the number of hardware and software technologies needed to manage networks, reduce network administration costs, and enhance cross-organizational collaboration and communications.
NetFlow analysis is just one part of a comprehensive network monitoring strategy. Integrating NetFlow data with other network monitoring tools, such as SNMP, syslog, and performance monitoring solutions, can provide a more holistic view of network performance and health.
How Kentik Helps with Netflow Analysis
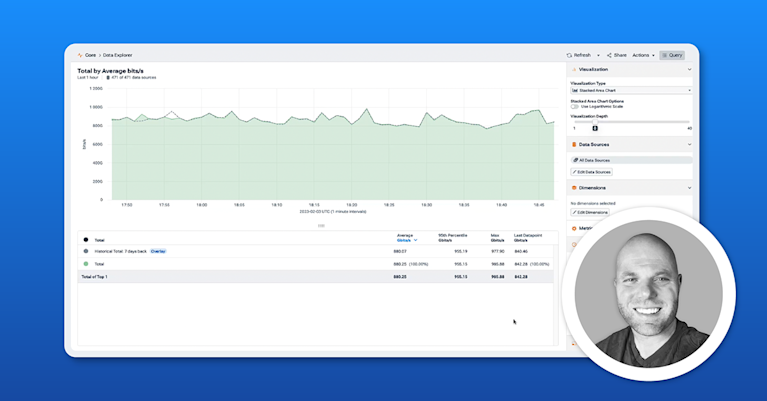
The Kentik Network Observability Platform provides a comprehensive view of network traffic flows, including hybrid and multicloud environments. By visualizing and analyzing network flow data, Kentik enables network professionals to understand traffic patterns, identify performance issues, and enhance security. Key features include:
- Real-Time Network Flow Monitoring: Visualize and analyze flow data in real-time across all network environments.
- Advanced Network Traffic Analytics: Identify anomalies and optimize network performance with detailed flow insights.
- Unified Dashboard: Monitor network paths, performance, and security from a single interface.
Kentik offers a suite of advanced network monitoring solutions designed for today’s complex, multicloud network environments. The Kentik Network Observability Platform empowers network pros to monitor, run and troubleshoot all of their networks, from on-premises to the cloud. Kentik’s network observability solution addresses all three pillars of modern network monitoring, delivering visibility into network flow, powerful synthetic testing capabilities, and Kentik NMS, the next-generation network monitoring system.
To see how Kentik can bring the benefits of network observability to your organization, request a demo or sign up for a free trial today.