Network Architecture Explained: Understanding the Basics of Modern Networks
In an era of increasing network complexity, understanding the ins and outs of network architecture is more crucial than ever. This article provides a comprehensive introduction to network architecture and its various components, bridging the gap between NetOps professionals and the general audience interested in the subject.
What is Network Architecture?
Network architecture defines the structured interaction between network services, devices, and clients to meet their connectivity requirements. It forms a blueprint dictating the layout, communication protocols, and connectivity patterns of network systems, functioning as a critical foundation for any digital environment.
Network architecture encompasses services like DHCP and DNS to cater to specific client needs. It includes diverse types such as access networks, facilitating intra-office connectivity; data center networks that provide data access and host applications; and Wide-Area Networks (WANs), enabling users to connect to resources over expansive distances.
Each architecture type is unique, with particular network security considerations, connectivity requirements, and service provisions. The significance of network architecture is twofold - ensuring efficient intra-network communication and fortifying against security threats. As a result, network architecture is a fundamental component in managing and designing any digital ecosystem.
Network Architecture vs. Internet Architecture
Network architecture and internet architecture are two related but distinct concepts. They may sound similar, but each has unique characteristics that set them apart.
Network architecture refers to the specific design and framework of a particular network. This includes how network devices and services are structured to cater to the connectivity requirements of the network’s users. It lays out the network’s structure, from hardware components like network routers and switches to protocols and services like DHCP and DNS. It’s about network design and constructing the network itself, focusing on efficient communication, secure data transfer, and performance optimization.
On the other hand, internet architecture describes the structure and protocols that make the global internet function. It doesn’t concern itself with individual networks but looks at how all networks interact to form the internet. Its focus is on the global system of interconnected computer networks and the protocols they use to communicate, such as TCP/IP.
While network architecture provides a network’s physical and logical design, internet architecture focuses on the global set of rules and standards that allow individual networks to work together as a coherent system—the internet.
The two architectures interact and complement each other. Network architecture lays the foundation for how devices and services interact within a particular network, while internet architecture provides the rules and protocols that enable these individual networks to interact and form the global internet.
To understand internet architecture better, let’s look at its layers: IP, TCP, and Application Protocol.
-
IP (Internet Protocol) Layer: The IP layer delivers packets from the source host to the destination host based on the IP addresses. This layer ensures that data is sent and received over the internet.
-
TCP (Transmission Control Protocol) Layer: The TCP layer provides reliable, ordered, and error-checked delivery of a stream of bytes between applications running on hosts communicating over an IP network. It is responsible for ensuring that data packets are transmitted without errors and in the correct order.
-
Application Protocol Layer: The Application Protocol layer contains all the higher-level protocols like HTTP (Hypertext Transfer Protocol), FTP (File Transfer Protocol), SMTP (Simple Mail Transfer Protocol), and others. These protocols are used by internet applications to send and receive data.
Each layer plays a crucial role in the functionality of the internet. The IP layer ensures the data gets to the right place, the TCP layer ensures the data is correct and in order, and the Application Protocol layer allows users to access and use the internet in a meaningful way.
Understanding network and internet architecture is critical for any professional involved in planning, designing, or managing network systems. This knowledge ensures that individual networks are designed and maintained effectively and that they can interact seamlessly with the larger internet system.
The definitive guide to running a healthy, secure, high-performance network

Understanding the Layers of Network and Internet Architecture: The OSI Model
In network architecture, networks are often considered to be composed of different layers, as described by the OSI model. The OSI (Open Systems Interconnection) model is a widely accepted framework that describes how different network protocols interact to provide network services.
While the OSI model consists of seven layers, for the sake of understanding network and internet architecture, we will focus on five essential layers: the application layer, transport layer, network layer, data link layer, and physical layer. Each layer performs a specific function and interacts with the layers above and below it.
Application Layer
At the top of the stack in the OSI model, the application layer (layer 7) provides an interface for users to interact with network services. This layer hosts various application-specific protocols like HTTP for web browsing, SMTP for email, FTP for file transfers, and DNS for domain name resolution.
Transport Layer
The OSI model’s transport layer, layer 4, ensures reliable data transfer. This layer utilizes two key protocols: TCP (Transmission Control Protocol), which offers reliable data transmission, and UDP (User Datagram Protocol), which provides faster but less reliable transmission.
Network Layer
Layer 3 in the OSI model, the network layer is responsible for routing data packets, i.e., deciding the most efficient path for data transfer from the source to the destination.
Data Link Layer
Layer 2 of the OSI model, the data link layer, is responsible for the reliable transmission of data frames between nodes on the same network layer. This layer establishes and terminates network connections, corrects errors that might occur at the physical layer, and decides how devices on the network share resources.
Physical Layer
The foundation of the OSI model, the physical layer (layer 1), is in charge of transmitting raw bitstreams over the physical medium. This includes the processes that physically transmit data and control the network interfaces on which data is transmitted. It deals with the mechanical, electrical, functional, and procedural characteristics of the physical connections between devices.
Key Components of Network Architecture Design
Network architecture design involves an intricate blend of components that must work harmoniously to deliver a reliable and efficient network. This involves hardware and software elements, which create a network capable of supporting an organization’s operations. To understand how these elements come together, let’s explore some of the key components in more detail:
Hardware
The hardware elements of network architecture design refer to the physical devices that facilitate communication within a network. These include:
-
Routers: Routers act as the postmasters of the network, directing data traffic. They connect networks and shuttle data packets between them based on the data’s destination IP address.
-
Switches: Switches are network traffic controllers that channel data to the correct device within a network. Unlike routers, switches operate within a single network.
-
Servers: Servers are high-powered computers that host data and applications that devices within the network can access. They can serve many roles, including file storage, hosting websites, or running applications.
-
Firewalls: Firewalls are the security guards of the network, protecting the network from unauthorized access and malicious attacks.
Network Protocols
Network protocols are sets of rules that govern how devices on a network communicate. They define how data is formatted, addressed, transmitted, and received. Some key network protocols include:
-
Internet Protocol (IP): IP is responsible for addressing and routing data packets so they can travel across networks and reach the right destination.
-
Transmission Control Protocol (TCP): TCP ensures data is reliably delivered across a network. It breaks data into packets, transmits them, and reassembles them at their destination.
-
User Datagram Protocol (UDP): Unlike TCP, UDP does not guarantee the delivery of packets, making it faster but less reliable. It’s often used for live streaming and gaming, where speed is more important than perfect accuracy.
Transmission Media
Transmission media refers to the physical or virtual paths by which data travels from one point to another in a network. There are two primary types of transmission media:
-
Wired: Wired networks use cables, most commonly Ethernet cables, to connect devices. These networks tend to offer faster data transfer rates and more security as they are less susceptible to interference and unauthorized access. However, they are less flexible due to the physical constraints of the cables, and their installation can require significant effort and resources, especially in large or complex environments.
-
Wireless: Wireless networks transmit data using radio waves (or, less commonly, infrared signals). The most prevalent forms of wireless networking are Wi-Fi and cellular data transmission protocols like 4G and 5G. These networks are highly flexible, allowing devices to connect from virtually anywhere within signal range, and are relatively easy to set up, as they require no physical cabling between devices. However, wireless connections generally offer slower data transfer rates than wired networks and may be more vulnerable to interference and security breaches. Implementing robust network security measures, such as Wi-Fi Protected Access (WPA3), is crucial when deploying a wireless network.
These transmission media serve as communication paths that link the nodes within a network. The choice between wired and wireless connections can significantly impact a network’s speed, reliability, security, and cost.
Network Topologies
The topology of a network refers to the physical or logical layout of the devices on the network. Modern networks have evolved significantly from traditional topologies, embracing more complex and efficient designs. Here are some of the modern network topologies:
-
Mesh Network Topology: Each device (node) is connected to every other network node, providing multiple paths for data to travel. Mesh networks offer robustness and redundancy, reducing the chances of network failure.
-
Hybrid Network Topology: This topology combines two or more different topologies to create a more complex and efficient network. It offers the benefits of each topology type it incorporates, enhancing reliability and ease of management.
-
Software-Defined Networking (SDN): SDN separates the control plane (making decisions about how data packets are routed) from the data plane (forwarding data packets based on these decisions). By managing the network centrally through software and separating the physical and logical layout of the network, SDN offers greater flexibility and easier management.
-
Peer-to-Peer (P2P) Network Topology: In P2P networks, interconnected nodes share resources without relying on a central server. This decentralized approach is common in file-sharing and distributed computing systems.
-
Tree (Hierarchical) Network Topology: This topology combines star and bus topologies, with multiple levels of devices connected hierarchically. It’s commonly used in wide area networks (WANs) and large-scale internetworks.
-
Virtual Network (Overlay Network) Topology: Virtual networks are created on top of existing physical networks and can have their own topology, independent of the underlying infrastructure. They offer flexibility and are often used for virtual private networks (VPNs) and software-defined wide-area networks (SD-WANs).
-
Cloud (Multi-tenant) Topology: In cloud-based network topologies, multiple organizations share the same network infrastructure provided by a cloud service provider. This topology offers scalability, flexibility, and cost savings.
-
Hybrid-Cloud Topology: This topology combines on-premises (private) and public cloud services. It offers scalability and flexibility while maintaining control and security over sensitive data and applications in the private cloud or on-prem infrastructure.
-
Multicloud Topology: While not, strictly speaking, a “topology,” multicloud is a strategy that integrates cloud services from multiple independent cloud providers, taking advantage of the distinct services and efficiencies of each. For example, a network might utilize AWS for machine learning, Google Cloud for analytics, and Azure for Microsoft product integration. Unlike hybrid cloud setups, each cloud in multicloud operates separately, focusing on maximizing the strengths of each provider.
Note that the traditional network topologies – bus, ring, and star – laid the foundation for these modern network designs, but more efficient and flexible topologies have largely supplanted them. The selection of network topology will depend on the specific needs and constraints of the network, such as cost, performance, security, and scalability requirements.
These are just a few components involved in network architecture design. A robust network architecture must consider all these elements and more, including network security protocols, network software, network services, and the network users’ needs. By understanding these components, network architects can design networks that are resilient, efficient, and capable of supporting the organization’s needs.
Public Networks vs. Private Networks: A Comparison
Public and private networks offer unique benefits and drawbacks based on their design and purpose. Public networks, being accessible to any user, are generally less secure but provide broad accessibility, which makes them suitable for information exchange on a large scale. Conversely, private networks are highly restricted, typically offering enhanced security and control over data. Organizations often prefer them to protect sensitive information and maintain privacy.
Benefits and Challenges of Different Network Architectures
Different network architectures cater to various needs based on their scale and reach, and each presents unique advantages and limitations. For example, Local Area Networks (LANs) provide high-speed connectivity and efficient data transfer within limited geographical areas, like offices or homes. Conversely, Wide Area Networks (WANs) offer broad coverage spanning cities or countries but at the cost of slower data transfer rates due to the large distances involved.
Common Types of Network Architectures
Networks can be structured to manage and control the flow of data and communication in various ways. The most common types (or styles) of network architecture include:
-
Peer-to-Peer (P2P): In a peer-to-peer network, all devices, often called “peers,” have equal capabilities and responsibilities. This architecture doesn’t require a central server, and all devices communicate directly with each other. The distribution of resources in P2P networks makes them potentially more resilient to failure than centralized architectures, as the failure of one node doesn’t significantly impact the entire network.
-
Client-Server: In a client-server architecture, some computers (servers) provide services, and other computers (clients) use those services. The server has more processing power and storage and performs most of the work. This centralization can make network maintenance easier but also presents a single point of failure.
-
Hybrid: Hybrid networks combine elements of the client-server and peer-to-peer architectures. Some devices in the network act as clients and access services, while others act as servers and provide services. Some devices fulfill both roles.
-
Cloud-Based Architecture: Cloud-based networks offer services and storage over the internet. Users don’t need to maintain their hardware and software; instead, they can access applications and storage provided by cloud service providers. This flexibility allows for easy scaling and global accessibility.
-
Software-Defined Networking (SDN): In an SDN architecture, the network’s control and forwarding functions are decoupled. This separation allows for centralized management and control over the entire network, promoting flexibility and rapid deployment of new services.
Types of Networks Based on Coverage Area
In addition to their architectural style, networks can also be classified based on their range or coverage area, such as:
Local Area Network (LAN): A LAN connects devices within a limited area like a home or office. It is efficient and offers high-speed connectivity.
Wide Area Network (WAN): WANs connect devices over larger geographical areas, such as between cities or countries. They are often slower than LANs due to the vast distance data has to travel.
Metropolitan Area Network (MAN): MANs connect users within a city. They’re larger than LANs but smaller than WANs.
Personal Area Network (PAN): PANs connect devices within an individual’s workspace or personal range.
The Internet (A Network of Networks): The internet is a global network of computer networks connected via TCP/IP protocols.
How Kentik Helps Network Architects
Kentik offers a robust network observability platform packed with features to help network architects design, manage, and optimize their network architecture:
-
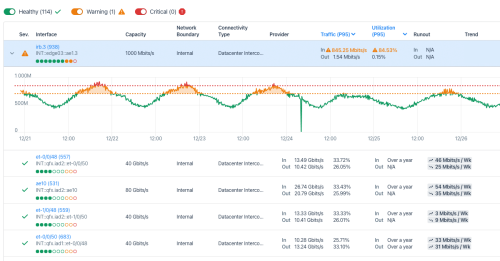
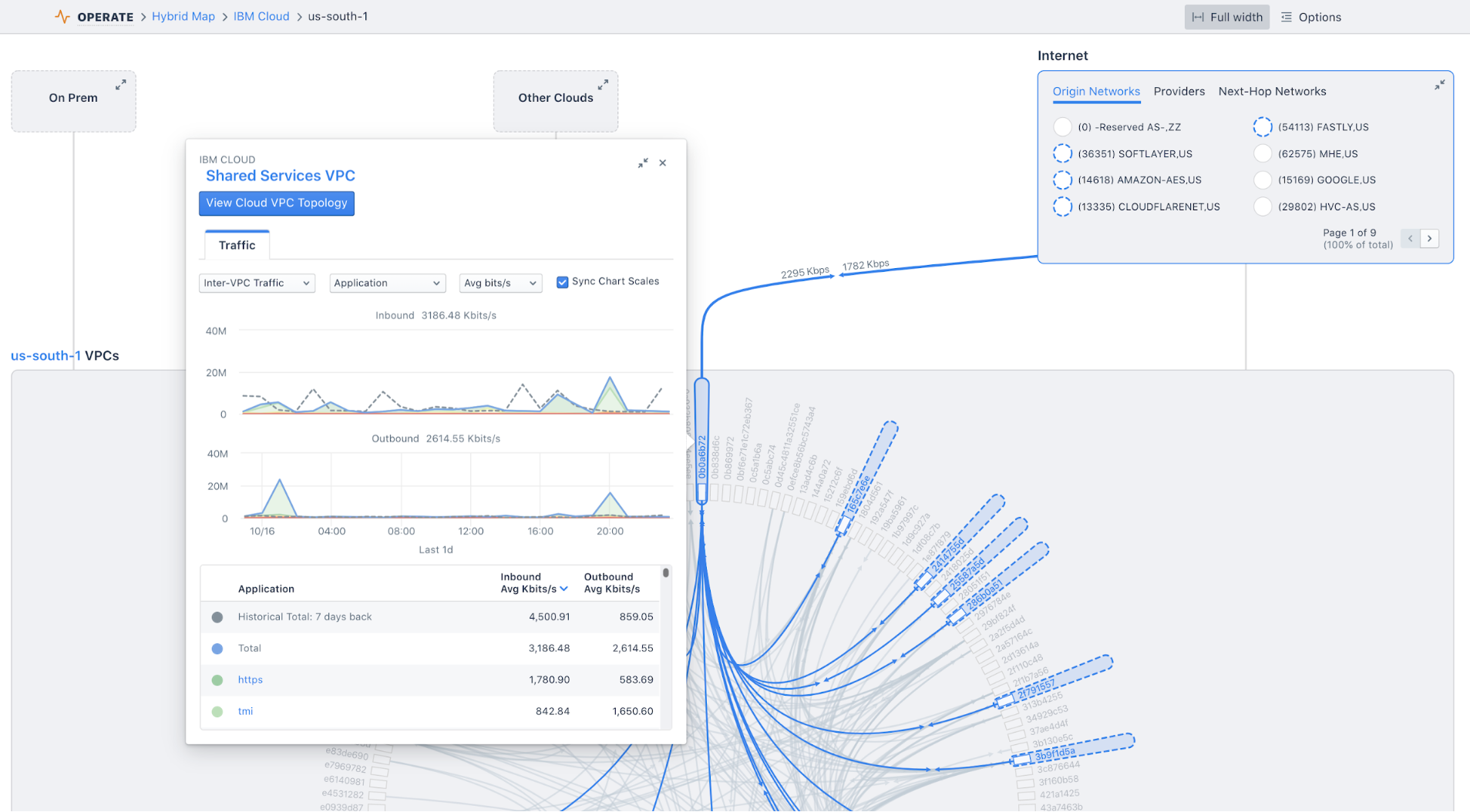
Kentik Map: This feature provides a visual representation of your network infrastructure, both on-premises and cloud-based. It helps architects quickly understand the interconnection of network components and their impact on traffic patterns, network health, and application delivery. Whether you’re dealing with hybrid network architectures or focusing on network health or traffic, Kentik Map gives you the clarity you need.
-
Network Capacity Planning: Kentik automates network capacity planning, offering growth forecasts and projected run-out dates. This enables architects to decide when to upgrade bandwidth or tweak network configurations for better optimization. From monitoring network provider capacity to advising clients on network upgrades, Kentik simplifies capacity management.
-
Discover Peers: With Kentik, network architects can monitor utilization trends on peering and transit interfaces, informing decisions about augmenting services or establishing new ones. Whether it’s identifying cost optimization opportunities, evaluating potential peering partners, or enforcing peering agreements, Kentik empowers data-driven decision-making.
-
Network Traffic Engineering: Kentik aids in BGP traffic engineering by identifying groups of prefixes impacting congested interfaces. It automates data collection and collation for traffic engineering tasks, precisely measures traffic impacts, and helps architects avoid capacity crises with its proactive, intelligent analysis.
-
Network Monitoring: By combining traditional network monitoring capabilities with modern network observability, Kentik NMS (Network Monitoring System) offers a powerful solution tailored for today’s complex network landscapes. Kentik provides extensible metrics collection and visualization, preconfigured for traditional network monitoring tasks. This system is designed to handle the scale of the largest networks in the world, seamlessly integrating SNMP monitoring and streaming telemetry. It represents a unified approach to network monitoring, combining efficiency and flexibility to cater to the needs of both enterprises and service providers.
Kentik’s network observability platform equips network architects with powerful tools to design, visualize, manage, and optimize network infrastructure. To see how Kentik can bring the benefits of network observability to your organization, start a free trial or request a personalized demo today.