SNMP Monitoring: An Introduction and Practical Tutorial
In this guide to SNMP Monitoring, we explore the foundations and practical applications of using Simple Network Management Protocol (SNMP) for network management. We cover the basics and history of SNMP, explore its metrics and versions, and provide a practical tutorial for setup and command execution. It also highlights best practices for SNMP monitoring and selecting monitoring tools that can help NetOps professionals ensure efficient, secure, and scalable network operations.
What is SNMP Monitoring?
An integral part of network management, SNMP Monitoring leverages the Simple Network Management Protocol (SNMP) to oversee and analyze network devices’ performance and health. It is a standardized approach enabling network engineers and administrators to efficiently collect crucial data from various networking equipment such as routers, switches, and firewalls.
The SNMP protocol, native to IP networks, is widely compatible with most network devices, providing a unified interface for diverse equipment. This compatibility ensures seamless information gathering across different vendor devices, promoting uniformity in network management.
Originating in 1988, SNMP was developed to establish a standard across all networking equipment, addressing the need for a consistent method to extract information, irrespective of the vendor. Over the years, its adoption has become almost universal, making it a cornerstone in network monitoring.
SNMP Monitoring Metrics
SNMP monitoring is used to track a wide variety of network device health and performance metrics, including:
-
Core Network Device Metrics: These are fundamental metrics that provide insights into the operational state of network devices. They include:
- CPU Usage: Indicates the processing power being utilized by a network device, which is essential for assessing its performance capacity.
- Memory Utilization: Helps in understanding the usage of RAM and other forms of memory, crucial for evaluating the device’s ability to handle current and future network loads.
- Disk Usage: Informs about the storage usage, which is vital for long-term data retention and overall device health.
- Bandwidth Utilization: Measures the amount of network traffic handled by the device, which is crucial to understanding its efficiency in data transmission.
- Uptime: Shows the duration for which the device has been operational without interruption, a critical indicator of network stability and reliability.
-
Network Error Metrics: These metrics shed light on potential issues within the network, such as:
- Dropped Packets: Indicates lost data packets during transmission, which can signal network congestion, hardware issues, or configuration errors.
- Packet Loss Rate: Helps identify packet loss frequency, impacting data transmission quality and network efficiency.
-
Hardware Device-Specific Metrics: Focuses on the physical aspects of network devices, including:
- Temperature: Monitors the operational temperature of devices, which is essential for preventing overheating and ensuring hardware longevity.
- Fan Speed: Helps assess the cooling efficiency of network devices, which is crucial for maintaining optimal operating conditions.
-
Non-Routable Interface Status: This metric refers to network interfaces that are not designed for routing traffic but are essential for local network management. Monitoring these interfaces is vital for:
- Ensuring the proper configuration and functioning of local management ports that may not participate in data routing but are crucial for device maintenance and management.
- Detecting issues with local connectivity or administrative access points, which might impact network management or security.
Each of these metrics plays an essential role in SNMP monitoring, offering network administrators a detailed view of their network’s performance, health, and potential areas for improvement. By closely monitoring these metrics, organizations can proactively manage their network infrastructure, ensuring optimal performance and minimizing downtime.
The definitive guide to running a healthy, secure, high-performance network

What is SNMP?
Simple Network Management Protocol (SNMP) is a crucial protocol within the Internet Protocol suite, playing a pivotal role in network management. Designed as an application layer protocol, SNMP provides a standardized framework for monitoring and managing the diverse components of a network.
At its core, SNMP facilitates communication between various network devices — from routers, switches, and firewalls to servers, printers, CCTV cameras, wireless systems, and any other network-enabled device — all connected over an IP network. Its primary function is to enable the efficient exchange of management information between network devices.
SNMP emerged in the 1980s, a time marked by significant growth and increasing complexity in organizational networks. It quickly established itself as a fundamental tool for network monitoring, widely recognized for its versatility and widespread acceptance across different network environments.
The protocol operates by gathering, organizing, and transferring network-related data. This data aids in fault detection and isolation, ensuring the stability and efficiency of the network. SNMP’s ability to seamlessly communicate between monitored endpoints and the monitoring system is central to its enduring relevance and utility in network management.
Network professionals gain a comprehensive view of their network’s health, performance, and security through SNMP, allowing for proactive maintenance and swift response to potential issues. Its simplicity and power in managing network devices, irrespective of their hardware or software, have solidified SNMP as a cornerstone in network management.
A Brief History of SNMP Versions
The journey of SNMP (Simple Network Management Protocol) through its versions coincides with the evolution of network management from basic to more secure and sophisticated mechanisms. Each version of SNMP brought enhancements aimed at addressing the needs and challenges of network management at the time.
SNMPv1 - The Pioneer
Introduced in 1988, SNMP version 1 (SNMPv1) laid the groundwork for network management protocols. As the first iteration, it offered a simple framework for monitoring and managing network devices. SNMPv1 operates within the structure of community strings, which act as a rudimentary form of authentication. Despite its simplicity and lack of robust security measures, SNMPv1 was widely adopted due to its ease of implementation and the immediate value it provided in managing diverse network devices.
SNMPv2 - The Evolution
SNMP version 2 (SNMPv2), emerging in the early 1990s, aimed to enhance the performance and security aspects where SNMPv1 fell short. SNMPv2 introduced improvements such as more efficient data encoding mechanisms and the concept of GetBulk requests, which significantly optimized data transfer for large-scale networks. However, SNMPv2 faced criticism for its security model, which led to the development of two sub-versions: SNMPv2c and SNMPv2u. SNMPv2c (community-based SNMPv2) continued using community strings for authentication, maintaining simplicity while incorporating the protocol enhancements. SNMPv2u (user-based SNMPv2) attempted to introduce a user-based security mechanism, although it saw limited adoption.
SNMPv3 - Enhancing Security
Recognizing the critical need for enhanced security in network management, SNMP version 3 (SNMPv3) was introduced in the late 1990s. SNMPv3 is a significant departure from its predecessors, strongly emphasizing security and privacy. It introduced a comprehensive security framework that includes authentication, privacy (encryption), and access control. These features allowed network administrators to securely manage devices across public and private networks, addressing the growing concerns over network vulnerabilities. SNMPv3’s adaptability to different security models and its scalability make it the preferred choice for modern network management tasks, despite its complexity compared to SNMPv1 and SNMPv2c.
The Ongoing Evolution of Network Device Metrics
The evolution from SNMPv1 through SNMPv3 reflects the adaptive nature of network management protocols to the changing landscape of network environments and security requirements. Each version of SNMP built upon the last, introducing necessary enhancements to meet the demands of increasingly complex and diverse network infrastructures. Today, SNMP remains a fundamental tool in network monitoring, with SNMPv3 offering the secure, robust framework necessary for modern network management.
SNMP is not the only protocol used in network device monitoring. More recently, streaming telemetry has emerged as a more efficient and higher-resolution way to collect network device metrics. It differs from SNMP in how it works, if not in the information it provides. Streaming telemetry solves some of the problems inherent in the polling-based approach of SNMP. The various forms of streaming network telemetry, such as gNMI, structured data approaches (like YANG), and other proprietary methods, offer near-real-time data from network devices. Because data is pushed in real-time from the devices and not polled at intervals, streaming telemetry can provide far higher-resolution data compared to SNMP. See our blog post for a more in-depth look at SNMP versus streaming telemetry
Understanding SNMP: A Practical Tutorial
If you do a search for “SNMP”, you’re likely to find a wide range of articles that tell you the history of SNMP and some vaguely helpful information on the relationship between the SNMP agent, MIBs, OIDS, Traps, and more.
What those articles don’t do a good job of is offer real-world, hands-on, easy-to-use instructions to help you learn about and build experience with SNMP.
But here at Kentik, SNMP is more than a theoretical or philosophical exercise. SNMP has real-world, present-day, measurable value, whether you’re monitoring elements on-premises or in the cloud. But that value can only be realized if you have a solid grasp of both what is possible with SNMP and how to execute the commands needed to realize those possibilities.
So let’s get started!
What You’ll Need for this Tutorial
We’ll begin by ensuring we have the right tools in place.
At the most fundamental level, you need to have a device from which you will collect SNMP information and the device that will do the collecting.
Many tutorials will show you how to do it all on the same system. While this is efficient, it also sets you up for frustration later because this doesn’t resemble anything like a real-world scenario. Therefore, when you get to the real world, you end up having to learn how to solve additional problems you never practiced.
So we’ll continue with a two-device scenario: You need a device that you’ll collect data from, and a different device that will do the collecting.
For our example, the device we will collect from is a printer (because most of us have one sitting around, and most printers will allow SNMP collection). And the device that will do the collecting is a system running some version of Linux. (A Raspberry Pi will also work fine. And sure, a Mac will also do.). While it’s possible to use a Windows system, there are a few extra steps, so we’ll stick with Linux for our purposes.
Once you have the two devices in hand, you need to make sure they can talk to each other — a simple ping test can do that:

Next, we need to make sure the printer has SNMP turned on and that we’ve set a community string.

Finally, we have to make sure SNMP is installed on the machine we’re going to collect from (i.e., where we are issuing the SNMP commands). On most systems, you must install the snmp-utils package, using the correct command for your operating system (apt, yum, brew, etc.).
One of the reasons we selected a printer for this example is because it has a graphical interface for the SNMP setup. The setup on most systems — especially network devices — will be more command-line driven. You shouldn’t let that dissuade you, but we wanted to make things as simple as possible for this first example.
Now that everything is in place, we’re ready to execute our first SNMP command!
Anatomy of an SNMP Command
To get SNMP information from a device, you’ll use the command snmpget. The most basic form of this command is:
snmpget -v <SNMP version> -c <community string> <machine IP or name> <SNMP object>
And because we know folks want to see something work, here’s a version of the command that will probably work, assuming you haven’t customized SNMP on your system too much. We’re also assuming the printer is at IP address 192.168.1.20.
snmpget -v 2c -c public 192.168.1.20 1.3.6.1.2.1.1.5.0

Whether it worked or not, let’s dissect that command a little:
- snmpget - the command itself.
- SNMP version - There are three versions of SNMP you will encounter. 1 is almost never used. 3 is used, but is far more complex in terms of authentication, which means you also don’t see it in the wild very often. And this blog isn’t going to cover it. 2c (and yes, you need the ‘c’) is the version you will find most often.
- Community string - Kind of like a password in the sense that it gives you access to a device. But NOT like a password in the sense that it’s transmitted in clear text and is utterly insecure.
- Machine IP or name - You can use the
snmpgetcommand (or any snmp command) using a machine name (myserver) or the IP address thatmyserverresolves to (192.168.1.20). Either is fine. - SNMP object - a dot-notated number that identifies the specific bit of information you are trying to collect. We’ll dive into Object IDs (OIDs) later on in this article.
So, let’s revisit that command. In plain English, we’re asking the machine 192.168.1.20, which is running SNMP version 2c, to give us the information represented by OID 1.3.6.1.2.1.1.5.0. And the community string is “public.”
The next question you probably have is, “How did you know that long SNMP OID number?” The answer to this is kind of a good news/bad news situation.
The good news is that OIDs come in well-documented, hierarchical structures that are easy to explore. The bad news is that there are about a bajillion OIDs, many of which are unique to a specific brand (or even model) of hardware and are not transferable.
Before you get too depressed, remember that “many… are not transferable” is not the same as “none… are transferrable”. There are plenty of OIDs that exist on most — if not all — devices. And 1.3.6.1.2.1.1.5.0 happens to be one of them. It’s better known by its common name: “sysName,” and it shows — as you should realize by now — the name of the system.
So… if you have no desire to dumpster dive through reams of documentation, how can you ever know which OIDs are valid for any type of device?
Going for an SNMPWalk
It’s actually possible to simply ask a device to divulge every single valid OID using the command snmpwalk.
WARNING: performing an SNMPwalk on a device is intensive and has been known to lock up certain devices if performed too many times in a row. It’s always better to do a walk and output the results to a file, so you can read the file later without having to re-perform the walk repeatedly.
The structure of snmpwalk is almost identical to snmpget:
snmpwalk -v <SNMP version> -c <community string> <machine IP or name>
Once again, because you want to try it first, here’s what that looks like “for real”:
snmpwalk -v 2c -c public 192.168.1.20

Now obviously, this is a very different beast than snmpget, where you get a single result back and go on with your life. What should strike you most is the utter lack of context. There’s just a list of OIDS and outputs (sometimes words, sometimes numbers, sometimes nothing).
The point of an snmpwalk is to walk numerically through every possible OID combination and show you which OIDs are valid (and what their current values are).
Which means your next question is probably, “How do I know what each of those numbers are?”
That’s where a MIB (Management Information Base) comes in. A MIB is the explanation of what each of the OIDs are showing. MIBs are created and maintained by the device manufacturer. For example, the start of the Brother printer MIB looks like this:

(You can find the complete MIB here.)
The upshot of all this is that you can use the MIBs to find the metric you want to collect. Then you can use SNMPwalk to make sure those OIDs are responding on the device, and you can use SNMPget to collect just that OID on an ongoing basis.
In future updates, we’ll expand on this tutorial with an overview of snmpgetnext, snmpbulkget, snmpbulkwalk, and other SNMP basics.
Know Better, Do Better
Now that you’ve had some hands-on experience with SNMP, there should be a question at the tip of your tongue: “Am I supposed to do all these commands for every system whenever I need to know something about how it’s doing?”
Of course not.
To be clear, these are the commands that need to happen, but that doesn’t mean you have to be the one to do it or that it needs to be done manually. This is where SNMP monitoring tools enter the picture. A robust SNMP monitoring and observability tool will be able to automatically:
- Discover the devices on your network
- Determine which OIDs are valid and responsive
- Collect, store, and display those values
… and to do all of that in ways that transform raw data into meaningful and actionable information.
Best Practices for SNMP Monitoring and Selecting SNMP Monitoring Tools
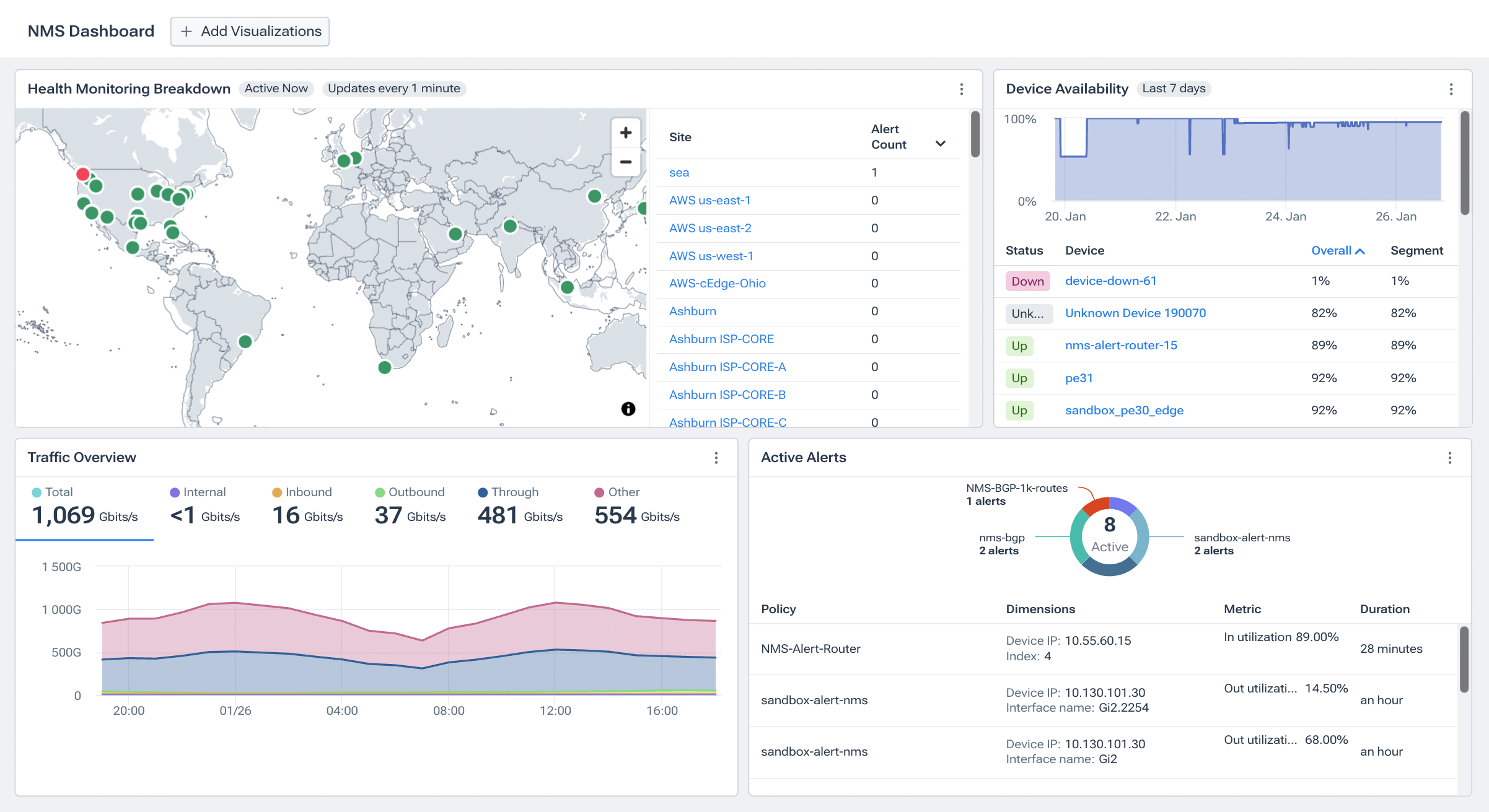
Effective SNMP monitoring is critical to ensuring network performance and reliability. It involves a blend of strategic monitoring techniques and the careful selection of network monitoring tools. Network professionals can create a robust, secure, and efficient monitoring framework by leveraging insights from advanced solutions like Kentik NMS and adhering to SNMP best practices. This approach helps in making informed decisions about both the strategies for SNMP monitoring and the criteria for selecting the right tools to meet the demands of modern networks:
-
Unified Telemetry Integration: Embrace platforms like Kentik NMS that provide a unified view of your network by integrating SNMP and streaming telemetry data. This unified approach offers comprehensive visibility, enhancing your ability to monitor and manage network devices efficiently.
-
Automated Network Discovery: Use solutions capable of automatically discovering and incorporating new devices into the monitoring framework. This ensures your network’s topology is always up-to-date, facilitating more accurate and efficient monitoring.
-
AI-Driven Analysis and Troubleshooting: Leverage AI and machine learning for advanced analytics and problem-solving. Tools that offer AI-assisted troubleshooting can significantly reduce mean time to resolution (MTTR) by quickly pinpointing and addressing network issues.
-
Scalable Solutions: Choose monitoring tools that can grow with your network. A scalable SNMP monitoring solution can adapt to increasing traffic volumes and device counts, maintaining performance without compromising detail or responsiveness.
-
Real-Time Data Collection: Prioritize systems that deliver real-time or near-real-time data. Immediate access to network performance metrics allows for swift decision-making and rapid response to emerging issues, keeping your network running smoothly.
-
Secure SNMP Practices: Regularly update SNMP community strings and consider using SNMPv3 for enhanced security features like authentication and encryption. Implement VLANs or dedicated network segments for SNMP traffic to isolate and protect management data.
-
Efficient Use of SNMP Traps: Configure SNMP traps for immediate alerts on critical network events. Traps can provide instant notifications about significant status changes or issues, enabling quicker responses to potential problems.
-
Comprehensive Documentation: Keep detailed records of your SNMP configurations, mappings, and architectures. Well-documented SNMP settings facilitate easier management, troubleshooting, and onboarding of new team members.
By incorporating these best practices into your SNMP monitoring strategy, you can achieve a more secure, reliable, and efficient network management system. Solutions like Kentik NMS further empower NetOps professionals by providing advanced features and capabilities tailored to the needs of modern, complex networks.
SNMP Monitoring with Kentik
Kentik’s suite of advanced network monitoring solutions is tailor-made for the complexities of modern, multicloud network environments. By addressing the three pillars of modern network monitoring—comprehensive visibility into network flow, robust synthetic testing capabilities, and a next-generation network monitoring system that supports both SNMP and streaming telemetry metrics—Kentik empowers network professionals to monitor, manage, and troubleshoot their networks with unparalleled depth and agility.
To see how Kentik can bring the benefits of network observability to your organization, request a demo or sign up for a free trial today.


